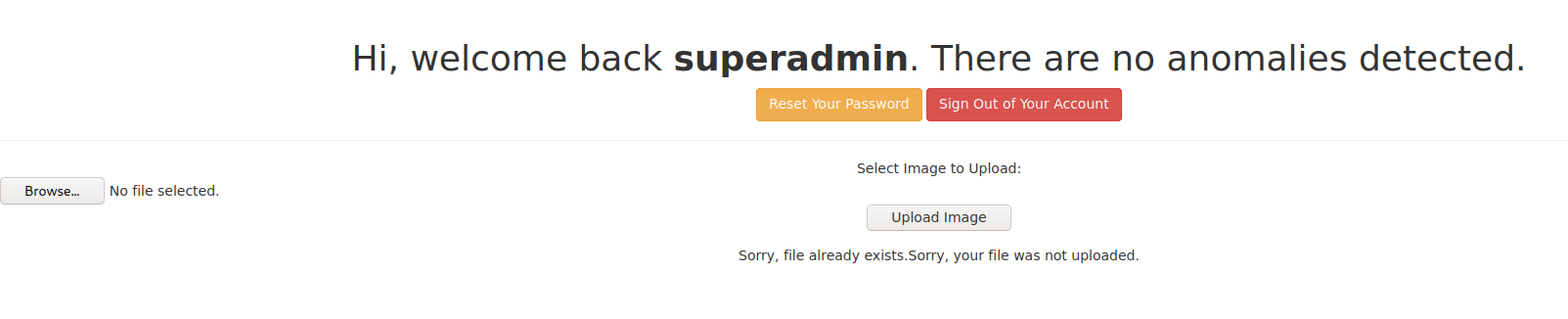
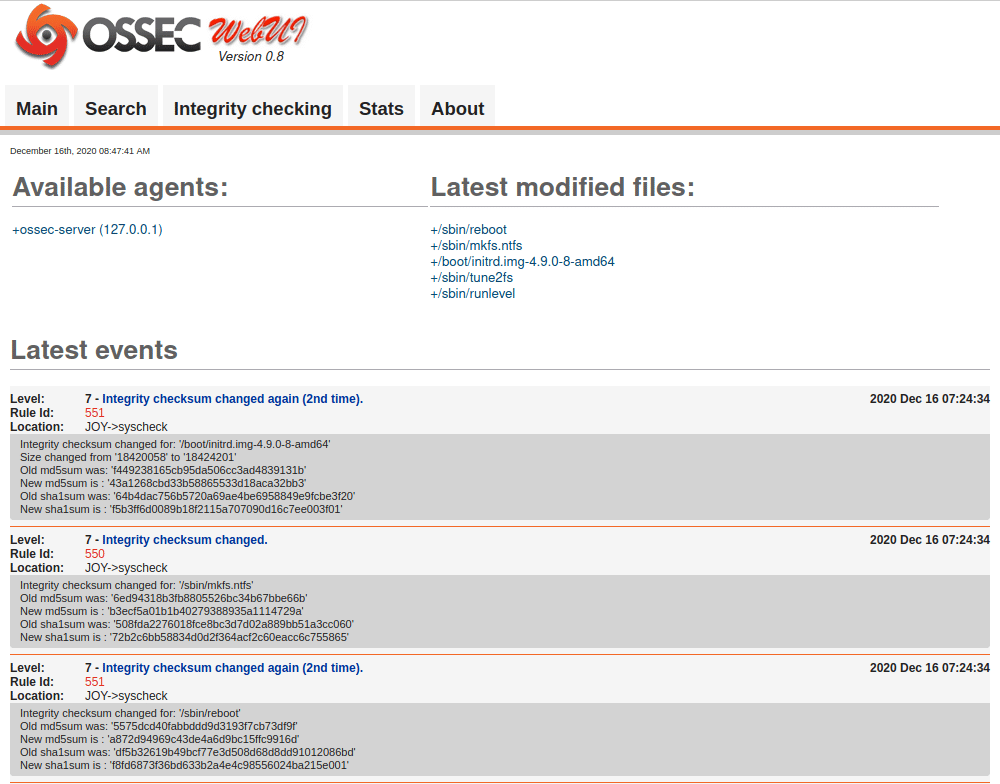
Vulnhub hackme walkthrough or writeup for an easy machine, step by step you will do the following: Download and run in VMWare workstation, identify the machine IP Scan the running services Web Enumeration and SQL Injection Exploit Get reverse shell Root the machine 1- Scanning nmap -A -p- 192.168.110.129 -oX hackme.xml -A aggressive scan ,
Vulnhub Hackme Walkthrough