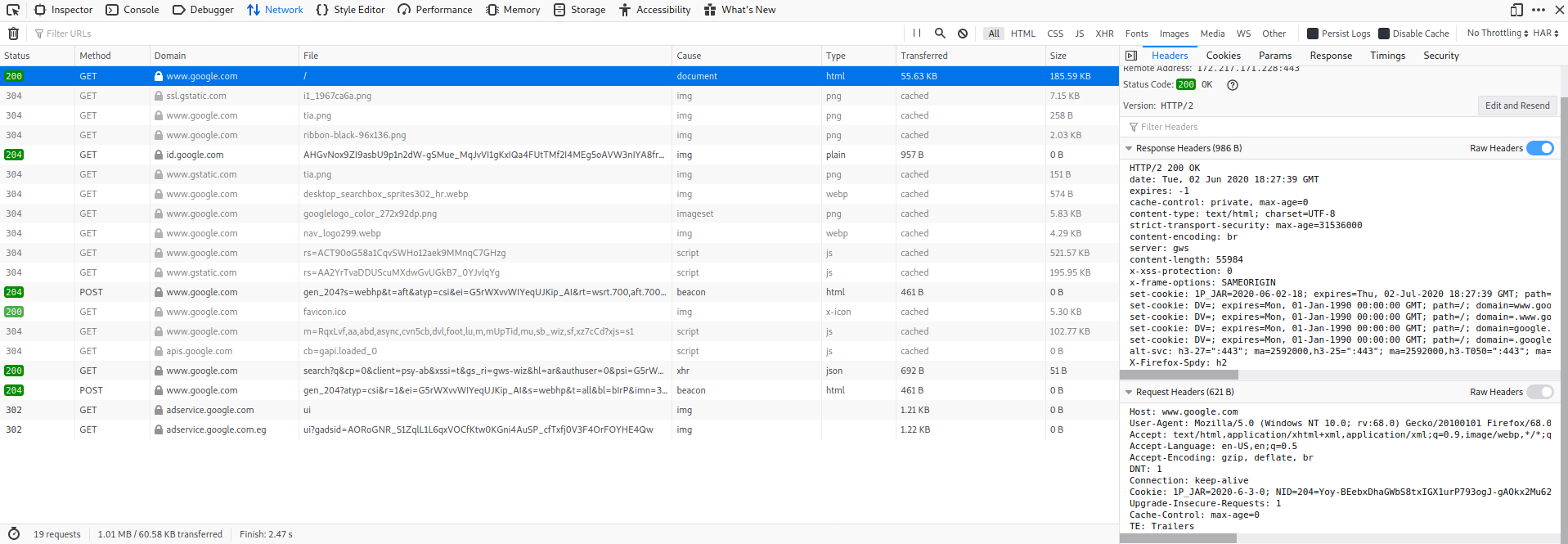
You can’t start web application penetration testing without studying the protocol that makes it happen, HTTP or its secure version HTTPS. So, What is HTTP Protocol ? HyperText Transfer Protocol, client-server protocol used to transfer web pages and web application data. The client and the server exchange messages [Clients Requests, server Responses] Web Clients: normally
Continue Reading “Web Application Penetration Testing – HTTP Protocol”