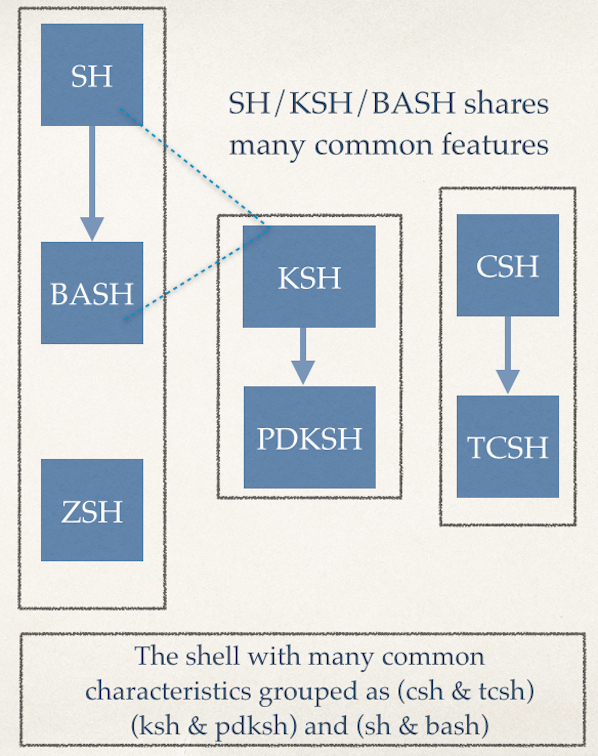
Since the Bourne Again SHell is a superset of sh, all sh commands will also work in bash – but not vice versa. bash has many more features of its own, and, as the table below demonstrates, many features incorporated from other shells.
sh vs bash vs ksh vs csh